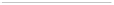Databases Reference
In-Depth Information
and each row in a table contains the same
fields
. Certain fields may be des-
ignated as data
keys
(not to be confused with “cryptographic keys”) when a
functional dependency or key constraint, holds for the table. Often, indexing
is deployed to speed up searches on values of such primary key fields. Data is
structured logically into valued
attributes
. From this perspective, a table is a
collection of such attributes (the columns of the table) and models a
relation
among them. The data rows in the tables are also called
tuples
. Data in this
model is manipulated using a
relational algebra
. Main operations in this alge-
bra are set operations (e.g., union, intersection, Cartesian product), selection
(of some tuples in tables) and projection (of some columns/attributes).
Rights protection for such data is important in scenarios where it is sensi-
tive, valuable and about to be outsourced. A good example is a data mining
application, where data is sold in pieces to parties specialized in mining it,
e.g., sales patterns database, oil drilling data, financial data. Other scenar-
ios involve for example online B2B interactions, e.g., airline reservation and
scheduling portals, in which data is made available for direct, interactive use
(see Figure 3). Given the nature of most of the data, it is hard to associate
rights of the originator over it. Watermarking can be used to solve this issue.
Data
Mining
outsourcing
...
...
...
...
...
...
...
...
...
...
...
STOP
Data
Rights
Holder
...
...
Third
Party
Fig. 3.
Rights Assessment is important when valuable data is outsourced to a third
party.