Databases Reference
In-Depth Information
as well as persons possessing accounts can be very dynamic. Determining
what application accounts make use of what database account requires an
inspection of the application programs, in case respective information is not
documented somewhere else. This process establishes application related sub-
paths
P
app
⊂U
p
×U
a
.
Information about database user accounts
U
db
, roles
R
db
, and database ob-
jects
DB
obj
can easily be obtained by querying the database's data dictionary.
If a database account
u
db
∈U
db
has directly been assigned some privileges on
object
o
db
∈DB
obj
, then sub-paths from
u
db
to
o
db
labeled with these privi-
leges can be determined. Similarly, if
u
db
has been assigned a role
r
db
∈R
db
,
then respective sub-paths are introduced from that role to database objects
the role is allowed to operate on. For the sake of simplicity, we again only
consider privileges with respect to relations and assume that if an account
u
db
or role
r
db
has insert, update, delete, or select privileges on a relation, then
there is only one suitably labeled sub-path from
u
db
and
r
db
to
o
db
, respec-
tively. If the same role
r
db
has been assigned to several database accounts,
then the sub-paths from
r
db
to database objects are only given once but there
are individual paths from these database accounts to
r
db
.
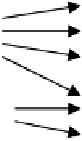
Figure 4 illustrates a case where a person
u
p
has an application account
u
a
,
and the application uses the database account
u
db
to connect to the database.
Two roles
r
db
and
r
db
are assigned to the account
u
db
, each with privileges on
different database objects
o
1
,...,o
5
.
o
1
o
2
o
3
r
db
u
p
u
a
u
db
o
4
o
5
r'
db
Fig. 4.
Instance of some access paths starting from a person
u
p
using an application
account
u
a
, which, in turn, has two roles
r
db
,r
db
with access privileges to some
database objects
o
1
,...,o
5
.
Gathering information about sub-paths from persons to database user
accounts and roles and representing these access structures and access cor-
relations to administrators can be supported by some kind of security re-
engineering workbench that, among other tasks such as the selective profiling
of data and users, allows to visualize different access paths. This simple rep-
resentation of access information can lead to some interesting insights, all of
which relate to the discovery of potential vulnerabilities in the current security
setup of the applications and the database. These include