Databases Reference
In-Depth Information
and methodology for a security re-engineering approach to databases, with a
focus on misuse and anomaly detection driven by data and user profiles.
4.2 Model Components
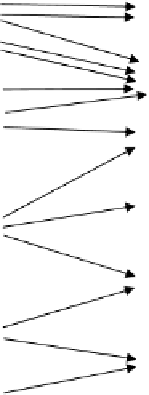
The access path model consists of several components that help describing
correlations between users and accesses at different layers. Figure 3 gives an
overview of the basic components, with applications and a single database as
back-end being the core components.
Applications
DB Objects
DB users
Person
Role
App
Account
Role
A
1
App
Account
Role
Role
App
Account
A
2
Role
App
Account
Role
A
3
App
Account
Role
Application Layer
Database Layer
Fig. 3.
Access Path Model
In this figure, there are three applications and several persons who have
access to the applications based on some application accounts. We assume
that a person does not directly connect to the database (e.g., at the database
server) but through an application once the she has been authenticated at the
application layer. We also make this assumption for DBAs, who operate on
the database only using administrative tools (applications). The connection
to the database occurs through database user accounts, which then, based
on the database privileges assigned to the accounts, are allowed to perform
operations on database objects. For the sake of simplicity, we only consider
operations on database relations, which are shown on the right. One could also
include other types of database objects, such as views or stored procedures,