Databases Reference
In-Depth Information
service request
Portfolio
Portfolio
request for prerequisites P
credentials/
credentials/
declarations
declarations
prerequisites P
State
State
requirements R request
permanent/
permanent/
negot.-dep.
negot.-dep.
re
quirements R' counter-req.
Policy
information
release
Policy
services/
info. release
R'
R
service granted
Client
Server
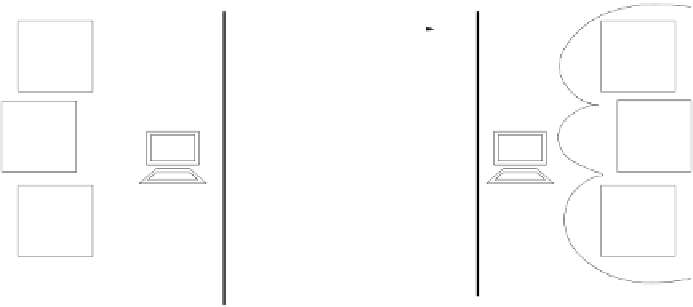
Fig. 5.
Client-server negotiation
The main advantage of this proposal is that it maximizes both server and
client's privacy, by minimizing the set of certificates exchanged. In particular,
the server discloses the minimal set of policies for granting access, while the
client releases the minimal set of certificates to access the resource. To this pur-
pose, service accessibility rules are distinguished in
prerequisites
and
requisites
.
Prerequisites are conditions that must be satisfied for a service request to be
taken into consideration (they do not guarantee that it will be granted); req-
uisites are conditions that allow the service request to be successfully granted.
Therefore, the server will not disclose a requisite rule until the client satisfies
a prerequisite rule. Figure 5 illustrates the resulting client/server interaction.
It is important to highlight here that, before releasing rules to the client, the
server needs to evaluate state predicates that involve private information. For
instance, the client is not expected to be asked many times the same informa-
tion during the same session and if the server has to evaluate if the client is
considered not trusted, it cannot communicate this request to the client itself.
4 Policy Composition
In many real word scenarios, access control enforcement needs to take into
consideration different policies independently stated by different administra-
tive subjects, which must be enforced as if they were a single policy. As an
example of policy composition, consider an hospital, where the global policy
may be obtained by combining together the policies of its different wards and
the externally imposed constraints (e.g., privacy regulations). Policy compo-
sition is becoming of paramount importance in all those contexts in which
administrative tasks are managed by different, non collaborating, entities.
Policy composition is an orthogonal aspect with respect to policy models,
mechanisms, and languages. As a matter of fact, the entities expressing the