Databases Reference
In-Depth Information
Document1 Document2 Program1
Program2
Ann
read, write
read
execute
Bob
read
read
read, execute
Carol
read, write
read, execute
David
read, write, execute read, write, execute
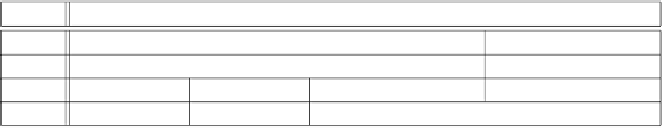
Fig. 1.
An example of access matrix
2 Classical Access Control Models
Classical access control models can be grouped into three main classes:
dis-
cretionary access control
(DAC), which bases access decisions on users' iden-
tity;
mandatory access control
(MAC), which bases access decisions on man-
dated regulations defined by a central authority; and
role-based access control
(RBAC), which bases access decisions on the roles played by users in the mod-
els. We now briefly present the main characteristics of these classical access
control models.
2.1 Discretionary Access Control
Discretionary access control is based on the identity of the user requesting
access and on a set of rules, called
authorizations
, explicitly stating which
user can perform which action on which resource. In the most basic form, an
authorization is a triple (
s, o, a
), stating that user
s
can execute action
a
on
object
o
. The first discretionary access control model proposed in the literature
is the
access matrix model
[4,5,6].Let
S
,
O
,and
A
be a set of subjects,
objects, and actions, respectively. The access matrix model represents the set
of authorizations through a
[
s, o
] contains the
list of actions that subject
s
can execute over object
o
. Figure 1 illustrates an
example of access matrix where, for example, user
Ann
can
read
and
write
Document1
.
The access matrix model can be implemented through different mecha-
nisms. The straightforward solution exploiting a two-dimensional array is not
viable, since
|
S
|×|
O
|
A
A
matrix
.Eachentry
A
is usually sparse. The mechanisms typically adopted are:
•
Authorization table.
The non empty entries of
A
are stored in a table with
three attributes:
user
,
action
,and
object
.
•
Access control list (ACL).
The access matrix is stored by column, that
is, each object is associated with a list of subjects together with a set of
actions they can perform on the object.
•
Capability.
The access matrix is stored by row, that is, each subject is
associated with a list indicating, for each object, the set of actions the
subject can perform on it.
Figure 2 depicts the authorization table, access control lists, and capability
lists corresponding to the access matrix of Fig. 1.