Information Technology Reference
In-Depth Information
which must expire before another attempt is made to transmit. This delay is not fixed, but is controlled by a random
number generator and so changes from transaction to transaction.
The probability of two node devices arriving at the same delay is infinitesimally small. Consequently if a collision
does occur, both devices will drop the bus, and they will start their back-off timers. When the first timer expires, that
device will transmit and the other will see the transmission and remain silent. In this way the collision is not only
handled, but is prevented from happening again.
The performance of Ethernet is usually specified in terms of the bit rate at which the cabling runs. However, this
rate is academic because it is not available all of the time. In a real network bit rate is lost by the need to send
headers and error-correction codes and by the loss of time due to interframe spaces and collision handling. As the
demand goes up, the number of collisions increases and throughput goes down. Collision- based arbitrators do not
handle congestion well.
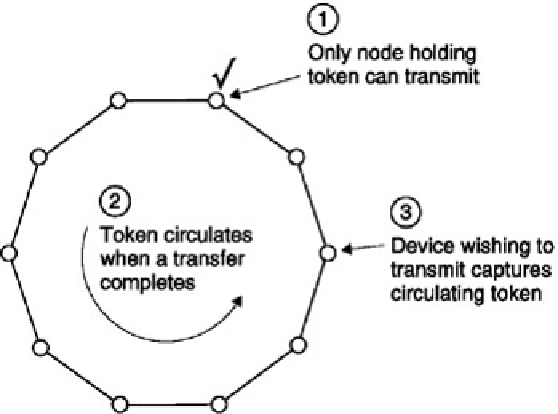
An alternative method of arbitration developed by IBM is shown in
Figure 7.26
.
This is known as a
token ring
system. All the nodes have an input and an output and are connected in a ring which must be complete for the
system to work. Data circulate in one direction only. If data are not addressed to a node which receives it, the data
will be passed on. When the data arrive at the addressed node, that node will capture the data as well as passing
them on with an acknowledge added. Thus the data packet travels right around the ring back to the sending node.
When the sending node receives the acknowledge, it will transmit a token packet. This token packet passes to the
next node, which will pass it on if it does not wish to transmit. If no device wishes to transmit, the token will circulate
endlessly. However, if a device has data to send, it simply waits until the token arrives again and captures it. This
node can now transmit data in the knowledge that there cannot be a collision because no other node has the token.
Figure 7.26:
In a token ring system only the node in possession of the token can transmit so collisions are
impossible. In very large rings the token circulation time causes loss of throughput.
In simple token ring systems, the transmitting node transmits idle characters after the data packet has been sent in
order to maintain synchronization. The idle character transmission will continue until the acknowledge arrives. In
the case of long packets the acknowledge will arrive before the packet has all been sent and no idle characters are
necessary. However, with short packets idle characters will be generated. These idle characters use up ring
bandwidth.
Later token ring systems use
early token release
(ETR). After the packet has been transmitted, the sending node
sends a token straight away. Another node wishing to transmit can do so as soon as the current packet has
passed. It might be thought that the nodes on the ring would transmit in their physical order, but this is not the case
because a priority system exists. Each node can have a different priority if necessary. If a high- priority node wishes
to transmit, as a packet from elsewhere passes through that node, the node will set
reservation bits
with its own
priority level. When the sending node finishes and tranmits a token, it will copy that priority level into the token.
In this way nodes with a lower priority level will pass the token on instead of capturing it. The token will ultimately
arrive at the high- priority node.
The token ring system has the advantage that it does not waste throughput with collisions and so the full capacity is
always available. However, if the ring is broken the entire network fails.
In Ethernet the performance is degraded by the number of transactions, not the number of nodes, whereas in token
ring the performance is degraded by the number of nodes.
7.8 FireWire