Information Technology Reference
In-Depth Information
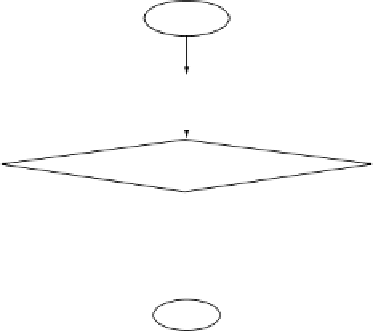
Begin
Input new samples
No
“Self!
Match any detector?
Yes
“Nonself!
End
Figure 4.3
Monitoring phase of an NSA.
A particular NSA is characterized by the way detectors are represented, the rule
used to determine the match between a sample and detectors, and the mechanisms
to generate and discard self-reactive candidate detectors. Most works on NSAs have
assumed one of the following schemes for encoding problem space: binary and real-
valued vector representation.
h e remainder of the sections are grouped under three parts: the fi rst part
(Sections 4.3 through 4.5) describes various detector generation schemes using
string representation in NSA algorithms, the second part (Sections 4.6 through
4.8) covers detector generation schemes for real-valued and hybrid representation,
and the third part (Section 4.9) covers the concepts of negative databases (NDB)
and algorithms to generate NDBs.
4.3 Negative Detector Generation Schemes
In string representation, each detector is represented as a string of fi xed length over
a fi nite alphabet (for binary, 0 and 1). Diff erent approaches have been developed
to generate negative detectors having varying degree of complexity. h e algorithm
described fi rst is an exhaustive approach, which appears to be analogous to the
natural NS process.
4.3.1
An Exhaustive Approach (Generating
Detectors Randomly)
In the original description of the NSA (Forrest et al., 1994), candidate detectors
were generated randomly and then tested (censored) to see if they matched any


Search WWH ::

Custom Search