HTML and CSS Reference
In-Depth Information
Introducing JavaScript
You meet with Kate to discuss her goals regarding the e-mail addresses on the library's
staff directory page. She shows you the content and page layout she has created.
To view Kevin's page:
◗
1.
Use your text editor to open
mpltxt.htm
from the tutorial.10\tutorial folder
included with your Data Files. Enter
your name
and
the date
in the comment sec-
tion at the top of the file and save the file as
mpl.htm
in the same folder.
◗
2.
Take some time to scroll through the document to become familiar with its con-
tents and structure.
◗
3.
Open
mpl.htm
in your Web browser. Figure 10-1 shows the initial appearance of
the Web page.
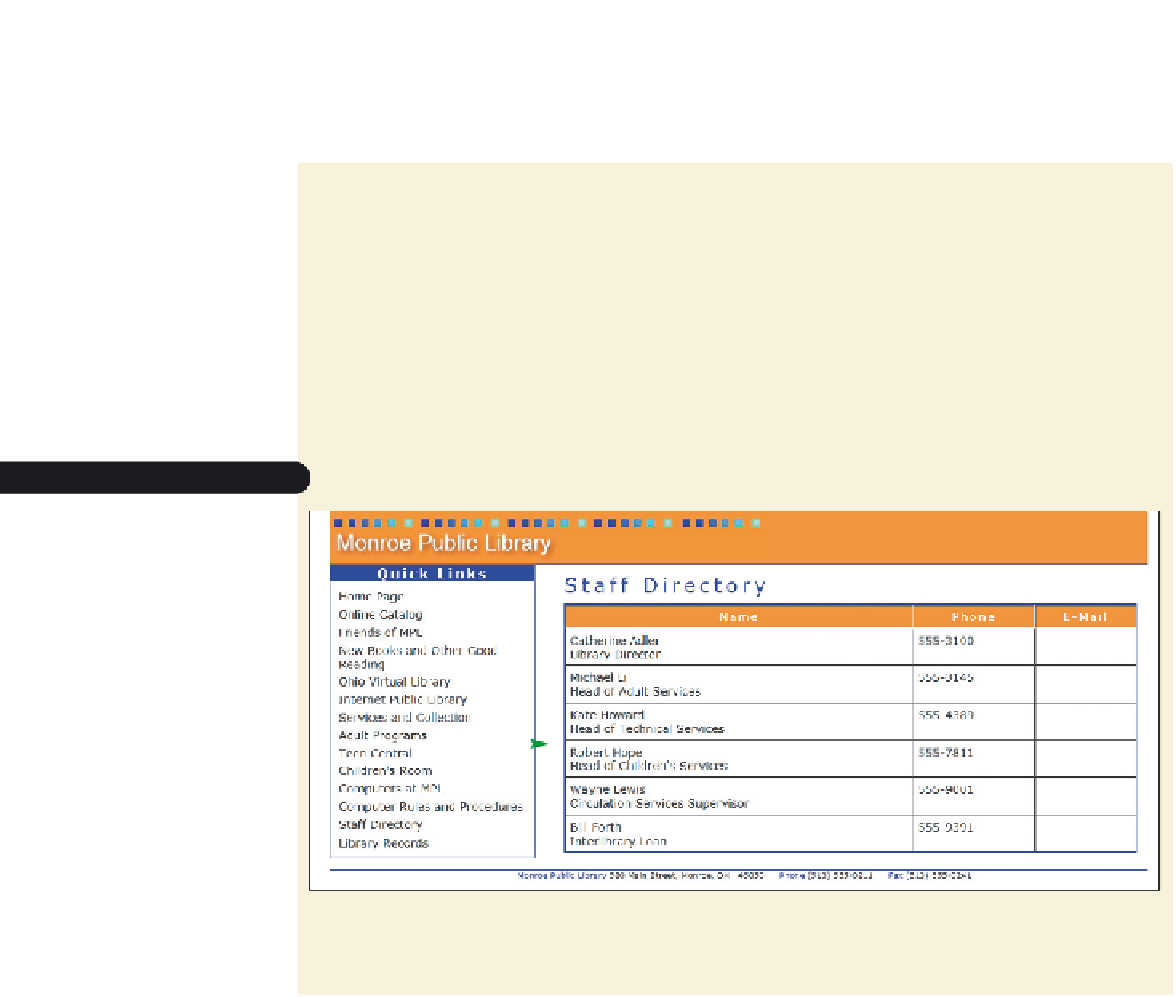
Figure 10-1
Monroe public Library staff page
column of e-mail
addre
s
ses to be
added to the
Web table
Note that the staff directory table contains a column in which Kate wants to insert
a link to each employee's e-mail address; right now the column is empty.
Although the staff directory page has proven invaluable in making library employees
more responsive to the needs of the public, Kate is concerned about the security risks of
putting e-mail addresses in the directory. Kate is most concerned about spam.
spam
is
essentially junk e-mail—messages that advertise products and services not requested by the
recipient. A
spammer
is a person who sends these unsolicited e-mails, sometimes in bulk
e-mailings involving tens of thousands of recipients. Aside from the annoyance of receiving
unsolicited e-mail, spam costs companies thousands—and sometimes millions—of dollars
each year by consuming valuable resources on mail servers and other devices forced to pro-
cess the messages. Spam also reduces productivity by forcing employees to wade through
numerous spam messages every day to find messages that are truly relevant. Even if your
spam filter hides unwanted e-mails from you, their mere existence costs millions of dollars
each year in the time spent by mail servers processing them.
One way that spammers collect e-mail addresses is through the use of e-mail harvest-
ers. An
e-mail harvester
is a program that scans documents, usually Web pages, looking
for e-mail addresses. Any e-mail address a harvester finds within the code of a document
is added to a database, which can then be used for sending spam. Thus, by putting the
staff's e-mail addresses in the HTML code for the staff directory, as in Figure 10-2, Kate
would also be making them available to e-mail harvesters.