Cryptography Reference
In-Depth Information
signatures, voice, or typing patterns. This class of identification techniques
is usually referred to as
biometrics.
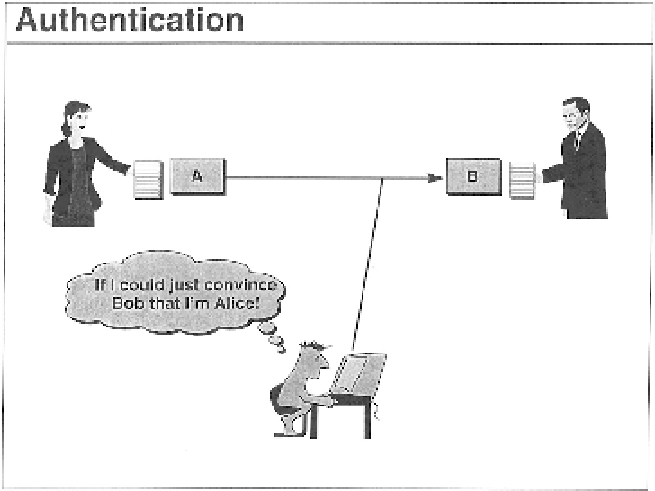
However, digital signatures do not as such provide for identification of
a signatory. Instead, they provide for
message authentication
, that is, evi-
dence that a given message has been encrypted with a certain private key
at some time in the past (see figure 4.3). The link between an individual
and her private key must thus be
presumed
. In practice, this is a multilay-
ered presumption: because users cannot be expected to remember 160-digit-
long prime numbers (category 1), these must be stored on smart cards or
computers (category 2), and access to the keys often granted through bio-
metrics mechanisms (category 3) or PINs (category 1). Nevertheless, by and
large, the field has not concerned itself with the means whereby users
achieve agency over their cryptographic keys and the risks associated with
such means. Indeed, given the overall orientation of modern cryptography
toward information in digital form, concerns with authentication through
passwords, physical documents, or biometrics are largely absent from the
cryptographic canon, relegated to the distinct field of
physical security.
Figure 4.3
Authentication and the corresponding threat of key substitution. Image courtesy of
Dr. Warwick Ford.