Cryptography Reference
In-Depth Information
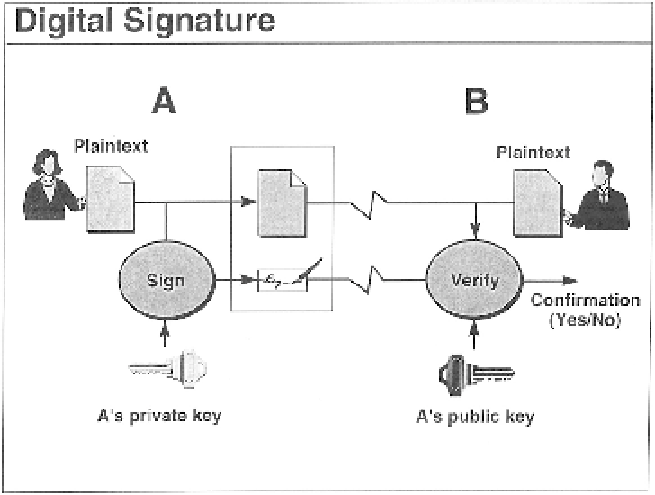
Figure 4.2
The digital signature model. Image courtesy of Dr. Warwick Ford.
public key is publicly available, anyone can decipher the message. But
given the unique mathematical relationship that obtains between the
public and the private keys, the receiver has confidence the message was
encrypted with the private key corresponding to Alice's public key and
furthermore, that it was not modified in transit, because otherwise the
decryption process would fail.
As noted before, Diffie and Hellman could not offer a concrete realiza-
tion of trapdoor one-way functions and thus, of digital signatures. The RSA
paper, “A Method for Obtaining Digital Signatures and Public-Key Crypto-
systems,” focused explicitly on the potential of public-key cryptography
for digital signatures. The signature algorithm it proposes fulfills the three
requirements outlined by Diffie and Hellman: (1)
unforgeability
: if the veri-
fication is successful, only the private key corresponding to the public key
obtained by Bob could have produced the signature; (2)
message dependence
:
if the message is modified after it is signed, the verification will fail; (3)
evidence in case of disputes
: neither Alice nor Bob can hope to modify the
message after it has been sent without the verification failing. The authors
recognized however that the translation of traditional concepts of “signa-
ture” and “proof” into the mathematical context required the cautionary