Cryptography Reference
In-Depth Information
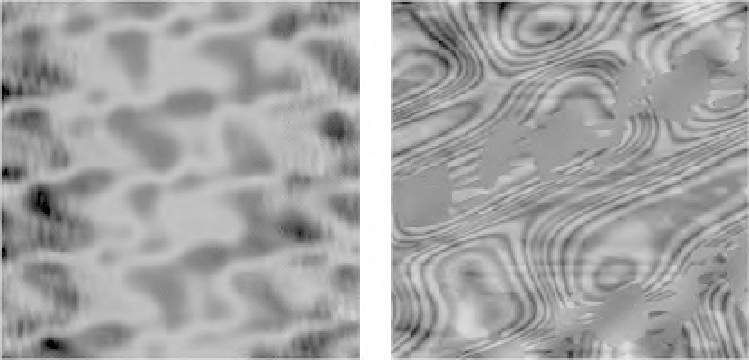
Figure 7.4
Two hash visualizations of public key fingerprints. The first hash is for fingerprint
51 86 E8 4E : 46 D7 B5 4E :: 29 D2 35 F4 : 41 89 5F 20; the second is for 51 86 E8
1F : BC B1 C3 71 :: B5 18 10 DB : 5F DC F6 20. From Adrian Perrig and Dawn Song,
“Hash Visualization: A New Technique to Improve Real-World Security,” in
Interna-
tional Workshop on Cryptographic Techniques and E-Commerce (CrypTEC'99)
(1999).
Used by permission.
functions
—blending metrics from cryptography and image processing—
can provide a more usable method for comparing public key fingerprints.48
48
Hash visualization functions build on the traditional requirements for
cryptographic hashing:
compression
, that is, a function
h
maps an input
bitstring
x
of arbitrary length to an output
y = h
(
x
)
,
a bitstring of fixed
length;
efficiency,
, that is,
h
(
x
) must be easy to compute;
collision resistance
,
the idea that it is not possible to invert the function, that is, given a bit-
string
y
, it is computationally infeasible to find the input
x
that corre-
sponds to
h
(
x
)
= y
.
Instead of outputting bitstrings, Perrig and Song suggest that hash func-
tions could just as well output images (see figure 7.4). With the help of
such a function, users could simply compare the hash visualization of their
browser's public key with the one published in a register to determine if
the key is authentic. The problem then becomes one of defining an appro-
priate metric of image equality and inequality. The authors propose a
measure of
nearness
: two images
I
1
and
I
2
are
near
(noted
I
1
≈
I
2
) if they are
perceptually indistinguishable.
Given such a metric, they can rewrite the
traditional definition of cryptographically hash functions as follows: