Hardware Reference
In-Depth Information
a
b
x/u
2
u
2
/o
1
u
3
/o
1
x/u
1
a
b
1
2
x/u
1
u
1
/o
1
u
2
/o
2
u
4
/o
2
u
3
/o
2
y/u
1
u
1
/o
1
u
4
/o
2
y/u
4
y/u
3
c
d
b
4
c
u
1
/u
1
u
4
/u
3
x/u
2
u
4
/u
4
u
1
/u
1
u
4
/u
2
,u
4
x/u
2
u
1
/u
2
,u
3
11
12
x/u
1
a
1
b
1
u
1
/u
1
u
2
,u
4
/u
4
u
1
/u
2
,u
3
u
1
/u
1
u
2
,u
4
/u
2
,u
4
u
2
,u
4
/u
3
y/u
2
y/u
2
x/u
1
x/u
1
u
2
,u
3
/u
1
u
2
,u
3
/u
2
,u
3
y/u
3
y/u
2
u
2
,u
3
/u
1
y/u
3
21
22
c
4
c
2
u
3
/u
2
,u
4
u
3
/u
4
u
3
/u
3
e
x/u
1
a
b
y/u
3
x/u
2
y/u
2
Fig. 5.3
Components (
a
) Head FSM M
A
and (
b
) Tail FSM M
B
of series topology M
A
!
M
B
of
Example
5.2
;(
c
) FSM M
D
that captures the flexibility at M
A
due to output don't care sequences;
(
d
) Submachine M
A
extracted from M
A
M
D
;(
e
) FSM M
0
A
obtained by state minimization of M
A
exists a pair of circuit implementations of M
B
and M
A
with no combinational cycles
created by connecting them together by the internal signals
u
and
v
. These DFSMs
are called
permissible
.
5.1.5
How to Exploit the Flexibility
A common way to exploit the computed flexibility is first to minimize the number
of states of each legal FSM and then the size of the logic realization of the encoded
FSM. State minimization of ISFSMs has been addressed in the classical literature



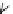




















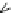
















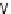

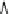








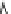

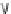






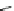


















Search WWH ::

Custom Search