HTML and CSS Reference
In-Depth Information
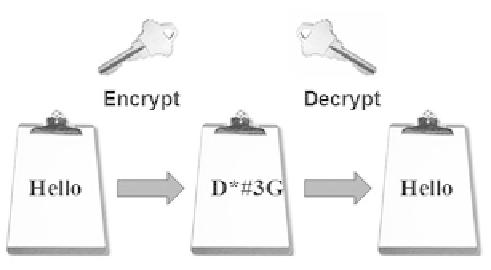
Figure 12.2
Symmetric-key
encryption uses a
single key
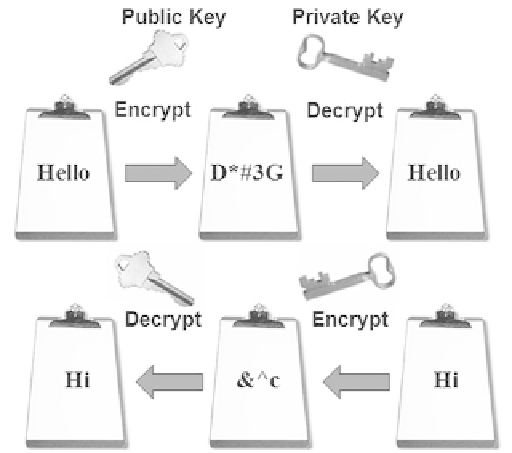
Asymmetric-Key Encryption.
Asymmetric-key encryption is also called public-key
encryption because there is no shared secret. Instead, two keys are created at the same
time. This key pair contains a public key and a private key. The public key and the pri-
vate key are mathematically related in such a way that it is unlikely anyone would guess
one of the pair even with knowledge of the other. Only the public key can decrypt a
message encrypted with the private key and only the private key can decrypt a message
encrypted with the public key (see Figure 12.3). The public key is available via a digital
certificate (more on that later). The private key should be kept secure and secret. It is
stored on the Web server (or other computer) of the key owner. Asymmetric-key encryp-
tion is much slower than symmetric-key encryption.
Figure 12.3
Asymmetric-key
encryption uses a
key pair
The encryption methods described above help to keep the contents of a message secret.
However, e-commerce security is also concerned with making sure that messages have
not been altered or damaged during transmission. A message is said to have
integrity
if
it can be proven that is has not been altered.
Hash functions
provide a way to ensure
the integrity of messages. A hash function, or hash algorithm, transforms a string of
characters into a usually shorter fixed-length value or key, called a
digest
, which repre-
sents the original string.
These security methods—especially the techniques of symmetric-key and symmetric-key
encryption—are used as part of SSL, the technology that helps to make commerce on
the Internet secure. The next section introduces this technology.

Search WWH ::

Custom Search