Java Reference
In-Depth Information
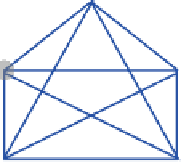
FIGURE 1.16
Point-to-point connections
connecting two geographically close computers, this solution works well and
is called a
point-to-point connection.
However, consider the task of connecting
many computers together across large distances. If point-to-point connections are
used, every computer is directly connected by a wire to every other computer in the
network. A separate wire for each connection is not a workable solution because
every time a new computer is added to the network, a new communication line
will have to be installed for each computer already in the network. Furthermore,
a single computer can handle only a small number of direct connections.
Figure 1.16 shows multiple point-to-point connections. Consider the number
of communication lines that would be needed if two or three additional comput-
ers were added to the network.
Compare the diagrams in Figure 1.15 and Figure 1.16. All of the computers
shown in Figure 1.15 share a single communication line. Each computer on the
network has its own
network address,
which uniquely identifies it. These addresses
are similar in concept to the addresses in main memory except that they identify
individual computers on a network instead of individual memory locations inside
a single computer. A message is sent across the line from one computer to another
by specifying the network address of the computer for which it is intended.
Sharing a communication line is cost effective and makes adding
new computers to the network relatively easy. However, a shared line
introduces delays. The computers on the network cannot use the com-
munication line at the same time. They have to take turns sending infor-
mation, which means they have to wait when the line is busy.
KEY CONCEPT
Sharing a communication line creates
delays, but it is cost effective and
simplifies adding new computers to
the network.
One technique to improve network delays is to divide large mes-
sages into segments, called
packets,
and then send the individual packets across
the network intermixed with pieces of other messages sent by other users. The
packets are collected at the destination and reassembled into the original message.
This situation is similar to a group of people using a conveyor belt to move a set
of boxes from one place to another. If only one person were allowed to use the
conveyor belt at a time, and that person had a large number of boxes to move,
the others would be waiting a long time before they could use it. By taking turns,





Search WWH ::

Custom Search