Java Reference
In-Depth Information
Enabling the Secure Socket Layer on JBoss AS
The JBoss AS uses the
Java Secure Socket Extension
(
JSSE
), which is bundled
in the J2SE to leverage the SSL/TLS communication.
An Enterprise application can be secured at two different locations: the HTTP level
for web applications and the RMI level for applications using EJB. HTTP communic-
ation is handled by the web subsystem within the
standalone.xml
/
domain.xml
file. Securing the RMI transport is, on the other hand, not always a compelling re-
quirement of your applications. Actually, in most production environments, JBoss AS
is placed behind a firewall.
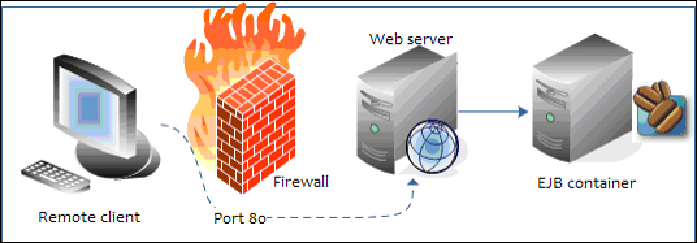
As you can see from the following diagram, this implies that your EJBs are not dir-
ectly exposed to untrusted networks, which usually connect through the web server
placed in a demilitarized zone:
In order to get started with the JBoss AS and SSL, we need a tool that generates a
public/private key pair in the form of an X509 certificate for use by the SSL server
sockets. This is covered in the next section.
Certificate management tools
One tool that can be used to set up a digital certificate is
keytool
, a key and certi-
ficate management utility that ships with the Java SE. It enables users to administer
their own public/private key pairs and associated certificates for use in self-authen-
tication (where the user authenticates himself or herself to other users or services)
or data integrity and authentication services, using digital signatures. It also allows