Java Reference
In-Depth Information
One significant issue with symmetric algorithms is the requirement of a safe admin-
istrative organization to distribute keys to users. This generally results in more over-
head from the administrative aspect while the keys remain vulnerable to unauthor-
ized disclosure and potential abuse.
For this reason, a mission-critical enterprise system usually relies on the asymmetric
encryption algorithms, which tend to be easier to employ, manage, and are ultimately
more secure.
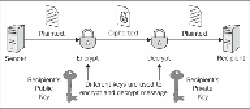
Asymmetric cryptography
, also known as
public-key cryptography
, is based on
the concept that the key used to encrypt is not the same as the key that is used to
decrypt the message. In practice, each user holds a couple of keys: the public key
that is distributed to other parties and the private key that is kept as secret. Each
message is encrypted with the recipient's public key and can only be decrypted (by
the recipient) with his private key:
Using asymmetric encryption, you can be sure that your message cannot be dis-
closed by a third party. However, there is still one vulnerability.
Suppose you want to exchange some valuable information with a business partner
and to that end are requesting his public key by telephone or by email. A fraudulent
user intercepts your email or simply listens to your conversation and quickly sends
you a fake mail with his public key. Now, even if your data transmission will be se-
cured, it will be directed to the wrong person!
In order to solve this issue, we need a document that verifies that the public key be-
longs to a particular individual. This document is called a
digital certificate
or public
key certificate. A digital certificate consists of a formatted block of data that contains
the name of the certificate holder (which may be either a user or a system name)
and the holder's public key, along with the digital signature of a Certification Authority
(CA) for authentication. The certification authority attests that the sender's name is
the one associated with the public key in the document: