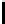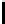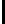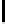Cryptography Reference
In-Depth Information
Table 16.1
An Exemplary Execution of the Quantum Key Exchange Protocol
1) 0 0 1 0 1 1 0 1 1 0
2) + x x + x + + x x +
3)
→→↑→→
4)
+
+
x
+
+
x
+
+
x
x
5)
0
1
0
00
0
1
1
0
6)
+
x
+
+
x
+
+
x
x
7)
OK
OK
OK
OK
OK
8)
0
1
0
0
1
9)
1
0
10)
OK
OK
11)
0
0
1
of A and B agree completely cannot be made arbitrarily close to one, unless most of
the bits are sacrificed. Both of these difficulties can be resolved by a protocol that
is commonly referred to serve the need of privacy amplification. This topic is not
further addressed (it is beyond the scope of this topic).
Last but not least, we note that the quantum key exchange protocol as dis-
cussed so far is also subject to the man-in-the-middle attack. An adversary can claim
to be B and use the quantum key exchange protocol to establish a key with A. Thus,
there must be out-of-band authentication mechanisms that A can use to properly
authenticate B.
16.5
FINAL REMARKS
In this chapter, we elaborated on some cryptographic protocols that two entities
can execute to establish a secret key. Among these protocols, key agreement pro-
tocols are particularly useful, because they allow both entities to participate in the
generation of the secret key. If this is not the case (such as in the case of a key
distribution protocol), then the quality of the secret key is bound by the quality of
the entity that actually generates the key. If this entity employs a cryptographically
weak PRBG, then the resulting secret keys may be weak. This happened, for ex-
ample, when the first implementations of the SSL protocol were found vulnerable
because the Netscape browser implemented such a cryptographically weak PRBG
(see Section 9.2 and the reference given therein). Contrary to that, all PRBGs of
all entities involved in a key agreement must be cryptographically weak, so that the
resulting secret key is weak.