Cryptography Reference
In-Depth Information
.K/
=
L
K
L
3
.K/
3
=
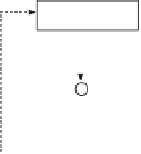
Figure 15.2
The PSS-R
Sign
algorithm.
the last part of
y
is
g
2
(
w
)
⊕
m
(instead of only
g
2
(
w
)). This means that
g
2
(
w
) is
used to mask the message.
Algorithm 15.6
The PSS-R
Recover
algorithm.
(
n, e, s
)
y ← s
e
(mod
n
)
break up
y
as
b w r
∗
m
∗
r ← r
∗
⊕ g
1
(
w
)
m ← m
∗
⊕ g
2
(
w
)
if (
b
=0 and
h
(
m r
)=
w
)
then output
m
else output
invalid
(
m
|
invalid
)
The PSS-R
Recover
algorithm is specified in Algorithm 15.6. Again, this
algorithm is similar to the PSS
Recover
algorithm. The major difference is that in
the PSS-R
Recover
algorithm the message
m
must be recovered from
m
∗
. This can
be done by adding modulo 2
g
2
(
w
) to
m
∗
. Also, the output of the algorithm depends
on a condition. If
b
=0and
h
(
m
r
)=
w
, then the PSS-R
Recover
algorithm
outputs
m
. Otherwise, it outputs one bit saying that the signature
s
is invalid. In this
case, the message is not recovered by the algorithm.