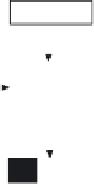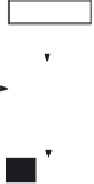Cryptography Reference
In-Depth Information
@
@
E
E
=
=
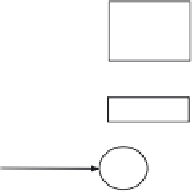
Figure 10.12
The working principle of the OFB mode.
Otherwise, the same key stream is generated, and this fact can be exploited by an
adversary. If, for example, two plaintext message blocks
m
i
and
m
i
are encrypted
with the same
r
-bit key
k
, then the resulting ciphertext blocks are
c
i
=
m
i
⊕
k
and
c
i
=
m
i
⊕
k
. Consequently, it is possible to add the two ciphertext blocks modulo 2
and remove the effect of the encryption accordingly:
c
i
(
m
i
⊕
c
i
⊕
=
m
i
⊕
k
)
⊕
k
)
m
i
⊕
=
m
i
⊕
k
⊕
k
m
i
⊕
=
m
i
⊕
0
m
i
=
m
i
⊕
If
m
i
is known, then
m
i
can be computed immediately (and vice versa). Even
if
m
i
is not known, the statistical properties of the plaintext language in use can
eventually be exploited to illegitimately determine
m
i
or parts thereof.
Finally, note that—contrary to the ECB and CBC modes—in the CFB and
OFB modes, both the sending and receiving devices use only the encryption function
of the underlying encryption system. This means that these modes of operation can
also be used if the encryption function is replaced with a one-way function (this
may be important if symmetric encryption systems are not available or if their use is
restricted in one way or another, respectively).