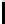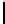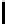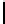Cryptography Reference
In-Depth Information
statements about the security of a Feistel cipher, unless one considers a particular
round function
f
. Let's elaborate on the DES encryption and decryption functions
or algorithms next.
10.2.1.2
Encryption Algorithm
DES is a Feistel cipher with
t
=32and
r
=16. This means that the block length
of DES is 64 bits, and hence
64
, and that the DES encryption
and decryption algorithms operate in 16 rounds. Furthermore, DES keys are 64-bit
strings with the additional property that the last bit of each byte is set to odd parity.
This means that the sum modulo 2 of all bits in a byte must be odd and that the parity
bit is set accordingly. This can be formally expressed as follows:
M
=
C
=
{
0
,
1
}
8
64
K
=
{
(
k
1
,...,k
64
)
∈{
0
,
1
}
|
k
8
j
+
i
≡
1(mod2) for
j
=0
,...,
7
}
i
=1
For example,
F1DFBC9B79573413
is a valid DES key. Its odd parity can be
verified using the following table:
11110001
F1
11011111
DF
10111100
BC
10011011
9B
01111001
79
01010111
57
00110100
34
00010011
13
Consequently, the first seven bits of a DES key byte determine the last bit, and
the size of the resulting key space is 2
56
(instead of 2
64
). As mentioned earlier, the
round keys derived from the DES key are the same for encryption and decryption;
they are only used in reverse order.
The DES encryption algorithm is specified in Algorithm 10.1 and illustrated
in Figure 10.1. To encrypt plaintext message block
m
using key
k
, the algorithm
operates in three steps:
1. The initial permutation (
IP
) as illustrated in Table 10.2 is applied to
m
.If
m
=
m
1
m
2
m
3
...m
64
∈M
64
,then
IP
(
m
)=
m
58
m
50
m
42
...m
7
∈
=
{
0
,
1
}
M
.