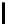Cryptography Reference
In-Depth Information
Algorithm 8.9
Round 4 of the MD5 hash function.
1.
A ←
(
A
+
i
(
B, C, D
)+
X
[0] +
T
[49])
←
6
2.
D ←
(
D
+
i
(
A, B, C
)+
X
[7] +
T
[50])
←
10
3.
C ←
(
C
+
i
(
D, A, B
)+
X
[14] +
T
[51])
←
15
4.
B ←
(
B
+
i
(
C, D, A
)+
X
[5] +
T
[52])
←
21
5.
A ←
(
A
+
i
(
B, C, D
)+
X
[12] +
T
[53])
←
6
6.
D ←
(
D
+
i
(
A, B, C
)+
X
[3] +
T
[54])
←
10
7.
C ←
(
C
+
i
(
D, A, B
)+
X
[10] +
T
[55])
←
15
8.
B ←
(
B
+
i
(
C, D, A
)+
X
[1] +
T
[56])
←
21
9.
A ←
(
A
+
i
(
B, C, D
)+
X
[8] +
T
[57])
←
6
10.
D
←
(
D
+
i
(
A, B, C
)+
X
[15] +
T
[58])
←
10
11.
C
←
(
C
+
i
(
D, A, B
)+
X
[6] +
T
[59])
←
15
12.
B
←
(
B
+
i
(
C, D, A
)+
X
[13] +
T
[60])
←
21
13.
A
←
(
A
+
i
(
B, C, D
)+
X
[4] +
T
[61])
←
6
14.
D
10
15.
C ←
(
C
+
i
(
D, A, B
)+
X
[2] +
T
[63])
←
15
16.
B ←
(
B
+
i
(
C, D, A
)+
X
[9] +
T
[64])
←
21
←
(
D
+
i
(
A, B, C
)+
X
[11] +
T
[62])
←
Ta b l e 8 . 3
Truth Table of the Logical Functions Employed by MD5
XYZ f ghi
0000001
0011010
0100110
0111001
1000011
1010101
1101100
1111110
2
30
√
2
=
0x5A827999
0
≤
t
≤
19
2
30
√
3
=
0x6ED9EBA1
20
≤
t
≤
39
2
30
√
5
K
t
=
=
0x8F1BBCDC
40
≤
t
≤
59
2
30
√
10
=
0xCA62C1D6
60
≤
t
≤
79
Note that the first two values correspond to
c
1
and
c
2
employed by MD4.
The preprocessing of the message to be hashed is identical to the one employed
by MD4 and MD5. Because the SHA-1 hash function was designed to run on a big-
endian architecture, the final two 32-bit words specifying the bit length
s
is appended
with the most significant word preceding the least significant word.