Cryptography Reference
In-Depth Information
other information of general interest. And new users select their password
themselves; taking some care nobody will know it.
All of this was thought out rather cleverly (not only for the level of the 1970s),
but two vulnerabilities remain:
1. When two users — a good one and a bad one — accidentally use the same
password, then each one of them can log in by the name of the other
user and get unlimited access to that user's files. The situation would
certainly be noticed and removed soon, but then it would be too late:
the bad user might have installed a Trojan horse, i.e., a program he can
use to get unauthorized access to the files of the good user, even if he
doesn't know the password since it had been changed.
2. There are circuits that implement the DES algorithm at very high speed.
This means that an attacker with appropriate hardware could mount a
brute-force attack and guess the password.
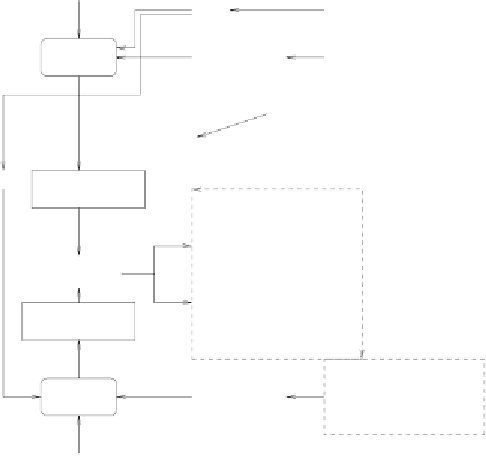
known plaintext
enter password
# passwd snoopy
New password:
Re-enter new password:
Salt
modif. 24-
round DES
password
as key
password file /etc /password or
/etc/shadow
entry
for
snoopy
Salt
search entry
encrypted
password
yes: login
COMPARE
no: deny
encrypted
password
login: snoopy
Password:
Login by
password query
modif. 24-
round DES
password
as key
known plaintext
Figure 3.4:
Password check during UNIX login.