Cryptography Reference
In-Depth Information
practically used keys
dictionary key
possible keys
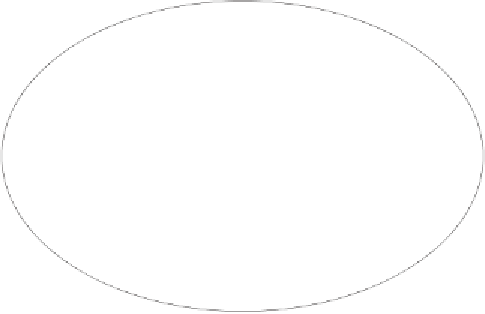
Figure 3.2:
Dictionary attack.
It is actually a cryptologist's highest goal to design his algorithm so well
that the cryptanalyst has to fall back on the brute-force method, for then
the attacker has generally little chance.
•
But we might not have to go that far. A dictionary attack might be
sufficient. People often take the request 'Enter your password' literally
and type a real password. In that case, ten thousand or hundred thousand
attempts will do to recover the key. There are plenty of corresponding
dictionaries available. This approach is appropriately called
dictionary
attack
. We will discuss a qualified attack of this type in Section 3.3.
Such
reduced key spaces
where the number of keys practically used is
much smaller than the number of keys theoretically possible are serious
ciphering errors. They are a major vulnerability in the symmetric methods
discussed so far.
This shortcoming can be removed reliably by using random session keys
(more about this in Chapter 4), or by crunching a passphrase such as
with PGP (see Section 7.1.3).
•
With methods working characterwise, which are most of the methods dis-
cussed so far, we will often use statistical methods. There were plenty of
examples in Chapter 2, and we will come back to this issue in Sections 3.5
and 3.6.
A prerequisite for such methods is the availability of sufficient statisti-
cal material. In view of the 'monster files' that current word processors