Cryptography Reference
In-Depth Information
identical MD5 hash sums (though these are not yet keys from prime-factor
products with an equal number of digits; the construction may only be a matter
of time, provided one would still be interested in it). This problem was done
away with in OpenPGP: from Version 4 (1998) onwards, it computes SHA-1
fingerprints.
It's always a good idea to accommodate the fingerprint on calling cards or publish
it in another print form, because it virtually excludes man-in-the-middle attacks.
Eventually, this is how a web of trustworthy partners is built. Sooner or later,
all PGP users will be interconnected by at least one 'path of trust'. A test
showed that the longest of these paths was only 14 steps long, considering that
there are hundreds of thousands of users!
The theoretical strength of this concept reflects Zimmermann's intentions: it is
virtually impossible for 'Big Brother' to destroy this web, as it is impossible
to totally control the Internet, because the links are established and torn down
locally and dynamically.
At the same time, this structure causes a major vulnerability: keys cannot
be securely revoked. If a private key is stolen, then the web's landscape
is disturbed, and even uninvolved users can be compromised. However, the
vulnerability cannot be exploited to attack the entire Web of Trust itself.
Alice
Hendrik
James
Susi
Marek
Egon
Kurt
Theo
Helmut
Bob
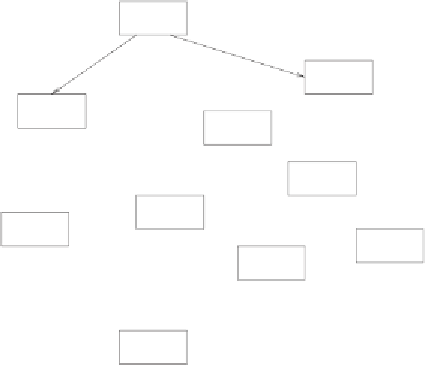
Figure 7.1:
The 'Web of Trust' of PGP. Thick arrows show full trust, whereas
thin arrows denote restricted trust.