Cryptography Reference
In-Depth Information
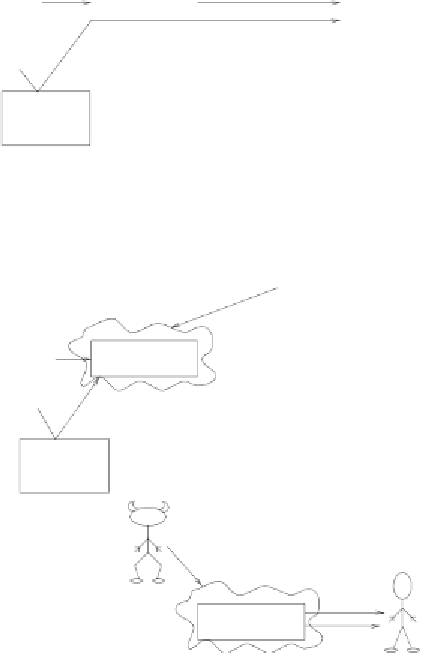
regular case:
customer
bank
Alice fills in the transfer slip
A
B
transfer
Alice supplies a valid password
Bob checks the password and
accepts the order
password
list
fraudulent maneuver:
M
Mallory pretends to be the bank
A
Alice fills in his transfer slip and
provides him with the valid password
transfer
password
list
M
Mallory pretends to be Alice
B
Bob receives a transfer slip and
Alice's valid password.
He accepts the order
transfer
Figure 6.8:
Home banking with one-time passwords and man-in-the-middle
attack.
signature on the correct, accepted password to the customer in a fourth step. But
in practice, a denial-of-service attack would be much harder than pretending to
be a bank computer anyway.
There are effective countermeasures even without digital signatures: if you are
doubtful of something, you simply write a transfer order for a non-existing
account and pass a wrong password along with it. No hacker can find this