Cryptography Reference
In-Depth Information
80
session key
IV
?
unit key
secret
checksum
function
SKIPJACK
?
?
32
80
16
unit ID
encrypted session key
checksum
SKIPJACK
global family key
128
L E A F
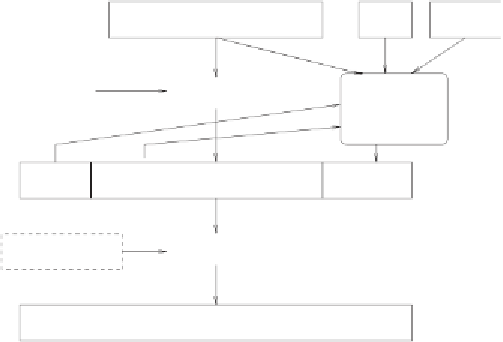
Figure 6.7:
Creating a LEAF in a Clipper or Capstone chip. The numbers
above the rectangles denote the width in bits.
Inventive Impostors
In the first attack, named
LEAF feedback
by Blaze, Alice and Bob agree to
outsmart the investigators. To this end, they slightly modify their software. The
following consideration shows them the way: even before a LEAF arrives at
Bob's, his chip already knows the session key, since it had been agreed upon
with Alice. Bob can now create a LEAF with this session key himself. He thus
gets an IV different from Alice's. Bob terminates the process and switches to
reception.
Alice doesn't send her LEAF along; Bob feeds his chip with the LEAF he
created himself instead. This LEAF is valid, since it belongs to the session
key, and the IV matches, too — so Bob's chip starts decrypting the session key
and Bob's IV.
But there is a problem: Alice's and Bob's IVs are different. The solution
depends on the ciphering mode used, which can be set in the Capstone chip.
You know the four most important ciphering modes from Section 5.1.1.
•
If Alice and Bob use the ECB mode, the IV doesn't matter, but this mode
is too insecure.
•
If they both use the CBC mode, then a faulty IV can cause only the first
64-bit block to decrypt wrongly. So Alice and Bob agree that the first