Cryptography Reference
In-Depth Information
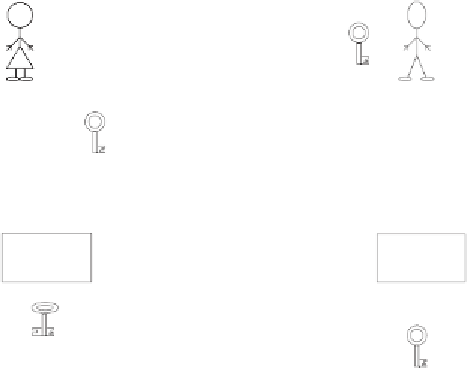
Alice signs
Bob checks
A
B
Alice's
public
key
Alice's
contract
Alice's
contract
DEcrypting
with Alice's
private key
ENcrypting
with Alice's
public key
data channel
Figure 6.4:
Using RSA for key exchange and signature.
an arbitrary text; second, the 'encrypt' and 'decrypt' operations have to be
interchangeable. RSA was the first asymmetric method well suited both for
key distribution and creating digital signatures.
This method meets Points 1 through 5 above. The security of the signature is
entirely based on the fact that the private key is never made known. However,
this method still has serious drawbacks.
•
Asymmetric methods are extraordinarily slow. This means that they can-
not be used to sign extensive documents.
•
The signed document is initially gibberish; it first has to be encrypted
with the public key — a time-consuming process. In practice, the signed
text will, therefore, normally be used as readable text where the signature
can no longer be checked. The risk of subsequent manipulations is high.
•
When signing third-party documents, a chosen-ciphertext attack against
RSA is possible (see Section 4.5.3). For this reason, a key pair different
from the one used for key distribution should be used for signing.