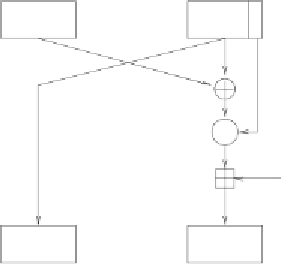
Cryptography Reference
In-Depth Information
L
i
R
i
XOR
r
rotation
S
i
addition
L
i+1
R
i+1
Figure 5.13:
Alternative representation of an RC5 round.
Choose two plaintext half blocks,
A
and
B
, and all subkeys,
S
i
, such that the
five least significant bits are each equal to 0. Then the last five bits of the
ciphertext half blocks are also equal to 0, which means that they certainly
won't depend on other key or plaintext bits. However, if the rotation occurs
even in one single round, the diffusion grows explosively. This might be one
of the reasons Rivest chose extremely 'odd' values for the initialization values,
P
w
and
Q
w
, and 'mixed in' the subkey field,
S
, extremely 'thoroughly'. With
12-round RC5 and random subkeys, the last five bits of all subkeys will be
equal to 0 only once in 2
130
cases. In mathematics, 2
−
130
is a positive number
indeed; for us humans, such a probability simply means 'never'.
The
confusion
is essentially determined by the data-dependent rotation. Any-
how, the security of RC5 depends essentially on the data-dependent rotation.
However, it has not yet been studied exhaustively.
RC5 was analyzed intensively at the RSA Laboratories. Statistically, the algo-
rithm has excellent properties — as may be expected. After only four rounds, the
single ciphertext bits depend 'equally' on the single plaintext bits (formulated
mathematically: the correlation almost no longer depends on bit positions).
During my own studies, I found no indication of statistically usable depen-
dencies. But this doesn't mean much. An algorithm with obvious statistical
dependencies is considered weak anyway.
According to information in [RivRC5], a trial with 100 million random plain-
texts and random keys showed that every plaintext bit influences a rotation
at least once (i.e., it influences the last five bits of a half block) after only
eight rounds.