Cryptography Reference
In-Depth Information
U
1
U
2
Z
5
Z
6
V
1
V
2
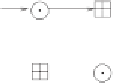
Figure 5.11:
The MA transformation forms the 'core' of IDEA.
then the same computations would be executed! This explains the meaning of
the output transformation in a very simple way.
Having made this discovery, we already know how to decrypt: we substitute
each key by the key that currently reverses the operation during the encryption.
These are the negative values of
Z
2
and
Z
3
, and the reciprocals modulo 2
16
+
1
with the others. XOR operations are self-inversing, i.e., applying them once
more to the same intermediate results produces the original result again. This
is why subkeys stand explicitly ahead of the '
+
' and '
' operations, but not
ahead of '
⊕
'!
That's cleverly designed indeed, but rather a technical question. We would
certainly accept a separate decryption algorithm for the price of higher security.
In contrast, another feature of IDEA is more interesting:
the result of an oper-
ation never becomes the operand of an operation of the same type in any place
.
No matter how we go along the arrows — two equal operations never follow
one after the other on one path. This is an important property of IDEA that has
caused
confusion
. But this confusion is 'more unfathomable' than with DES,
at least subjectively.
There
are
more
remarkable
properties
in
IDEA.
In
its
core
is
the
MA
(multiplication - addition)
transformation
, shown in Figure 5.11.
The MA transformation is responsible for
diffusion
. Computer experiments have
shown that, with this transformation,
every bit of
V
1
and
V
2
depends on every
bit of the keys and every bit of blocks
U
1
and
U
2
. And all this after one single
round! Lai and Massey also showed that at least four operations are required
to achieve this — so the MA transformation is even minimal in this sense.