Cryptography Reference
In-Depth Information
In general, there are two specific points where we have to be particularly careful
when creating keys: when session keys are generated automatically, and when
keys are entered manually. We will deal with the first point in the next section.
Creating Session Keys—ANSI X9.17
If you have a secret corner on your computer that really nobody can look into,
then I recommend you to create keys based on ANSI standard X9.17 (published
in 1985). Though this standard specifies DES only as block cipher, you can
use any other block algorithm. As usual, we denote
E
K
(E
=
encryption) as
the encryption with key
K
below.
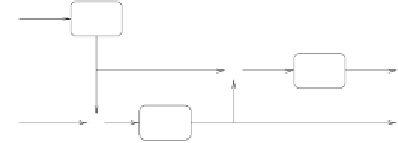
Using this ANSI standard, we define a very secret key,
K
, and a secret initial
value,
V
. We store the two values in that secret corner on our computer.
The procedure creates keys continually. In every step we have to determine a
timestamp,
T
(more about it below), and compute a key,
S
:
⊕
S=E
K
(E
K
(T)
V)
Subsequently, we determine a new
V
:
V=E
K
(E
K
(T)
⊕
S)
and also put it away in the secret corner (Figure 5.6).
If the bit count of
S
does not coincide with the number of bits required for
the key, we delete bits from
S
, or create several
S
keys and concatenate them.
secret key
K
“time stamp”
E
K
T
E
K
V
new Initialization
Initialization
E
K
V
S
key created
Figure 5.6:
Creating session keys according to ANSI standard X9.17.