Cryptography Reference
In-Depth Information
Initialization
block
C
1
C
2
C
3
IV
. . . ciphertext blocks
DES
DES
DES
. . . encryption
P
1
P
2
P
3
. . . plaintext blocks
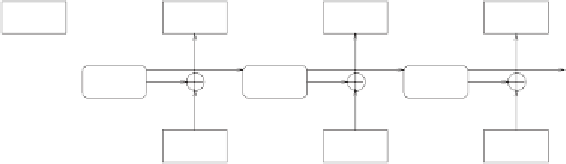
Figure 5.3:
Ciphering in OFB mode.
Compared with CFB, this mode has an important benefit in some situations:
the sequence (
S
n
) can be computed independently of the plaintext. This is
interesting for online encryption over fast message channels, of course, but also
for optional access: if all interesting
S
n
blocks are cached in main memory,
or if they can be computed fast, we could pick out arbitrary ciphertext blocks,
C
n
, and decipher them immediately. This is exploited by the
crypted file system
(CFS) under UNIX (see Section 7.4); it also lets you encrypt databases.
However, the OFB mode is dangerous: when the same key and the same ini-
tialization vector,
S
0
, are used to encrypt two different texts, and an attacker
knows parts of a plaintext, then he can use these parts and the pertaining
ciphertext passages to easily XOR-compute the corresponding key blocks. The
attacker can then learn parts of the remaining plaintext. This is the reason why
every data stream must have a different
S
0
. This is necessary also to prevent a
possible active attack; more about this in the following section.
Protection Against Active Attackers
It is well known that cryptanalysts try to get unauthorized hold of plaintexts
and/or keys. Conversely, active attackers may not do any cryptanalysis at all
(but have to have an understanding of it); they actively intervene in the data
traffic, trying to exploit things to their liking.
For example, an intranet is often connected to the outside world over one sin-
gle computer. This computer (often only the special software on it) is called
a
firewall
, since it is supposed to protect the internal network against hacker
attacks from the outside like, well, a firewall. The administrator of this firewall