Cryptography Reference
In-Depth Information
CBC got its name because the ciphertext blocks are XOR-chained with the
plaintext.
CFB: Cipher Feedback Mode
To encrypt data traffic between a central computer and its terminals by means
of a block algorithm, neither the simple ECB mode nor the better CBC mode
can be used. Imagine you press the ENTER key at such a secure terminal and
wait for a command to be executed. Like all characters, this ENTER is also
subject to an encryption algorithm. But this algorithm works with 64-bit blocks,
and your ENTER character is the second character in the block just started.
You can quietly go get yourself a cup of coffee — nothing will happen. The
only solution would be to append seven arbitrary bytes to each character and
then send this block immediately. That would cause an eightfold increase of
the data traffic, which is undesirable, of course.
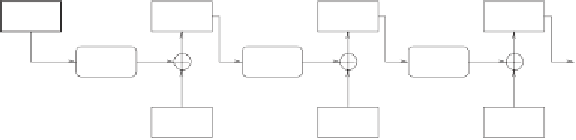
The CFB mode comes in handy here, because it uses a block cipher as a stream
cipher. It's also pretty simple: the ciphertext block produced in the previous
section is re-encrypted and XORed with the plaintext block. The result is the
new ciphertext block. Mathematically, it looks like this:
C
n
+
1
=P
n
+
1
⊕
DES(C
n
).
(The names remain the same as with the CBC mode; as a reminder, 'DES'
stands for a block algorithm; see Figure 5.2.) Again, we begin with a random
initialization vector,
C
0
. But we can now encrypt every byte (and even bit)
of
P
n
+
1
instantly, because DES(
C
n
) is known. Once the eight plaintext bytes
from
P
n
+
1
are read and encrypted, we compute DES(
C
n
+
1
), and start the game
Initialization
block
. . . ciphertext blocks
C
1
C
2
C
3
IV
. . . encryption
DES
DES
DES
. . . plaintext blocks
P
1
P
2
P
3
Figure 5.2:
Ciphering in CFB mode.