Cryptography Reference
In-Depth Information
Of course, this is a malicious, fabricated example. Still, we should bear it in
mind. Product algorithms can have excellent properties, but they have to be
studied as critically as all others. Mixing things or creating plain 'chaos' is
never
a guarantee for security.
4.2 Feistel Networks
Many of the product algorithms currently used are so-called
Feistel networks
.
They were described by Horst Feistel (IBM) and first published in the 1970s
[Feistel]. The underlying principle is rather simple, only you don't initially see
how it could be useful.
We split each block into two equal halves and denote the left half of the block
as
L
i
and the right half as
R
i
in the
i
th round. Depending on a secret key,
S
,
we can compute a function,
f
S,i
, that converts half blocks to half blocks. The
actual encryption consists in that we swap the two half blocks, and XOR
L
i
and
f
S,i
(R
i
)
:
L
i
1
=R
i
+
R
i
1
=L
i
⊕
f
S
,
i
(R
i
)
(1)
+
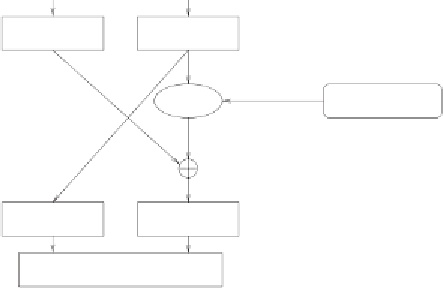
This is graphically represented in Figure 4.6.
plaintext block
R
i
L
i
f
round's key
L
i+1
R
i+1
ciphertext block
Figure 4.6:
A round in a Feistel network.