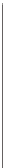Cryptography Reference
In-Depth Information
STAND
ERCHB
KFGI L
MOPQU
VWXYZ
Figure 2.4.
Example of a Playfair Square
2. We write out the plaintext as a sequence of pairs of letters:
NA TT ER IA CK TO AD
.
3. We observe that the second bigram consists of TT, so we must insert a Z in
between the two Ts, to get NATZTERIACKTOAD.
4. We rewrite the modified plaintext as a sequence of pairs of letters:
NA TZ TE RI AC KT OA D
,
and note that there are now no bigrams with repeated letters.
5. Finally, we need to addaZtotheendinorder to complete the last bigram:
NA TZ TE RI AC KT OA DZ
.
We then proceed to encrypt these bigrams as follows:
1. The letters of the first bigram NA lie together in the same row of the Playfair
Square in Figure 2.4, so NA is encrypted using this square to DN.
2. The letters in the next bigram TZ do not lie together in the same row or column.
They thus define the corners of a rectangle in the Playfair Square. The encryption
rule says that in this case they are encrypted to the two letters occurring at the
other two corners of this rectangle. Thus TZ is encrypted to DW. Similarly, TE is
encrypted to SR, and RI is encrypted to HF.
3. The letters AC lie in the same column, so they are encrypted to CG.
4. The letters KT do not lie in the same row or column, so KT is encrypted to FS.
Similarly, OA is encrypted to PT.
5. Finally, DZ lie in the same column, so are encrypted to BD (note that since Z is
in the last row, it is encrypted to the letter in the first row, D).
The final ciphertext is thus DNDWSRHFCGFSPTBD.
To decrypt this ciphertext, the receiver will reverse the encryption process
using the Playfair Square in Figure 2.4 to obtain NATZTERIACKTOADZ. They
will hopefully 'guess' that the two Zs are redundant and remove them to recover
NATTERIACKTOAD. A knowledge of European amphibians should then allow
the correct plaintext to be obtained!