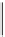Cryptography Reference
In-Depth Information
User
Authentication centre
RAND
RAND
SIM
A3
A3
RES
K
i
K
i
Check?
A8
A8
K
c
K
c
Encrypted data
A5/1
A5/1
Phone
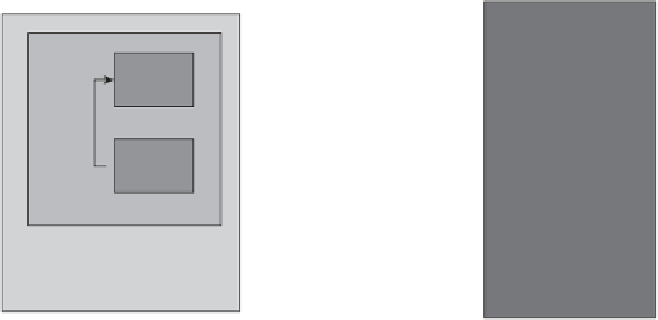
Figure 12.7.
GSM authentication and encryption
3. Alice's SIM card uses
K
i
and
RAND
to compute a response
RES
using
algorithm A3:
RES
=
A
3
K
i
(
RAND
)
.
The response
RES
is sent back to Bob.
4. Bob, who maintains a database of all the user keys, selects the appropriate key
K
i
for Alice and then computes the expected response in the same way. If the
result matches the received
RES
then Alice is authenticated.
5. Alice and Bob both use
K
i
and
RAND
to compute an encryption key
K
c
using
algorithm A8:
.
This simple protocol relies on the belief that only the mobile user and the mobile
operator authentication centre can possibly know the key
K
i
that has been installed
on the user's SIM card.
K
c
=
A
8
K
i
(
RAND
)
GSM ENCRYPTION
While authentication is a service that is 'private' to a mobile user and their mobile
operator, encryption must be provided using a mechanism that is common to all
mobile operators, in order to facilitate cross-network calls. Thus the encryption
algorithm A5/1 is fixed by the GSM standard (in fact GSM offers three different
versions of A5, but A5/1 is the most commonly deployed). As indicated in
Figure 12.7, it is implemented on the mobile phone itself, not the SIM card,
since the phone has more computation power than the SIM.
The A5/1 algorithm is a stream cipher with a 64-bit key. It was designed to be
implemented very efficiently in the hardware of a mobile phone. In GSM, A5/1 is