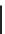Cryptography Reference
In-Depth Information
Terminal
Host
key register
key register
Derive transaction key
K
request ||
MAC
K
(request)
Derive transaction key
K
response ||
MAC
K
(response)
Update key register
Update key register
key register
key register
Figure 10.5.
Generic UKPT scheme
2. How should the transaction key be derived so that the terminal and host derive
the same key?
3. How should the terminal key register be updated so that the terminal and host
update to the same value?
There are various ways in which these operations could be conducted in such a
way that the terminal and host stay synchronised. Two examples of real UKPT
schemes are:
Racal UKPT scheme
. This scheme answers the three questions as follows:
1. The initial value is a secret seed, which is agreed between the terminal and the
host.
2. The host maintains an identical key register to the terminal. The transaction key
is derived from the key register and the card data (more precisely, the primary
account number on the card), both of which are known by the terminal and the
host.
3. At the end of the protocol, the new key register value is computed as a function
of the old key register value, the card data (primary account number) and the
transaction data (more precisely, the two
MAC residues
of the MACs on the
request and response messages, both of which can be computed by the host
and the terminal but neither of which are transmitted during the protocol, see
Section 6.3.3). Both the terminal and the host conduct the same computation
to update their key registers.