Cryptography Reference
In-Depth Information
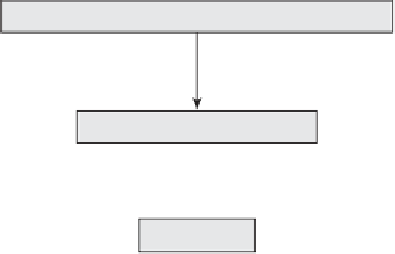
Master keys
Key encrypting keys
Data keys
Figure 10.2.
A three-level key hierarchy
the management of the top-level keys 'right', the management of the rest of the
keys can be taken care of using the key hierarchy.
A SIMPLE KEY HIERARCHY
The idea of a key hierarchy is best illustrated by looking at a simple example. The
'simple' example shown in Figure 10.2 provides a key hierarchy that is probably
good enough (and maybe even more complex than necessary) for the majority of
applications. The three levels of this hierarchy consist of:
Master keys
. These are the top-level keys that require careful management. They
are only used to encrypt key encrypting keys. Since the key management of
master keys is expensive, theywill have relatively long lifetimes (perhaps several
years).
Key encrypting keys
. These are distributed and stored in encrypted form using
master keys. They are only used to encrypt data keys. Key encrypting keys will
have shorter lifetimes than master keys, since they have greater exposure and
are easier to change.
Data keys
. These are distributed and stored in encrypted form using key
encrypting keys. These are the working keys that will be used to perform
cryptographic computations. They have high exposure and short lifetimes.
This may simply correspond to the lifetime a single session, hence data keys
are often referred to as
session keys
.
Since the longevity of the keys in the hierarchy increases aswe rise up the hierarchy,
it is often the case that so does the length of the respective keys. Certainly keys
at one level should be
at least as long
as keys at the level beneath. Note that
the 'middle layer' of key encrypting keys may well be unnecessary for many
applications, where it suffices to have master keys and data keys.
MANAGING THE TOP-LEVEL KEYS
Top-level (master) keys need to be securely managed, or the whole key hierarchy
is compromised. Most keymanagement systems using key hierarchies will employ