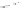Cryptography Reference
In-Depth Information
Suppose that Alice wishes to send a secure message to Bob, whom she has
not met before and with whom she has no previous trust relationship. As this is
a physical message, Alice will secure it by locking it in a briefcase. By 'secure',
we mean that we want to make sure that nobody can see this message during its
transportation (in other words, we want confidentiality over the communication
channel). As Alice has not had any prior trust relationship with Bob, we assume
that Bob does not already share a key with Alice. Figure 5.1 shows that, perhaps
surprisingly, establishment of some sort of a secure channel is possible.
1. Alice begins by obtaining a padlock. Only Alice has the key to this padlock.
2. Alice places the message into the briefcase, locks the briefcase using the
padlock and hands the locked briefcase to a courier, who transports it to Bob.
3. Bob obtains a padlock of his own. Once Bob receives the briefcase, he adds a
second lock to the briefcase and returns the briefcase to the courier, who takes
it back to Alice.
4. Alice removes her padlock and hands the briefcase to the courier, who once
again transports it to Bob.
5. Bob removes his padlock and opens the briefcase to obtain the message.
The briefcase protocol achieves our stated goal because the message is kept
confidential throughout its three journeys between Alice and Bob, since the
briefcase is always locked by at least one padlock belonging to either Alice or
Bob. Although this version secures a physical message, it is possible to produce a
cryptographic equivalent of the protocol shown in Figure 5.1.
Alice
Bob
1
2
3
4
5
Figure 5.1.
The briefcase protocol