Cryptography Reference
In-Depth Information
plaintext
1
L
0
R
0
key
K
2
f
⊕
3
⊕
5
L
1
=
R
0
R
1
=
L
0
f
(
R
0
,
K
)
4
key
K
6
⊕
f
⊕
L
2
=
R
1
R
2
=
L
1
f
(
R
1
,
K
)
7
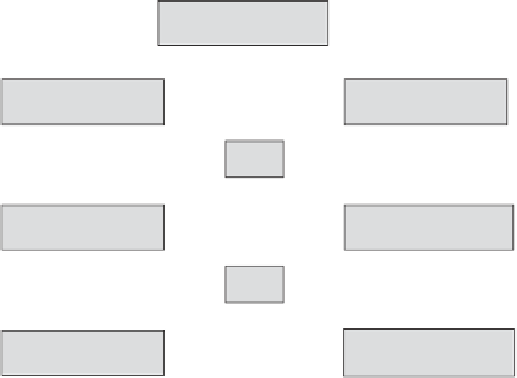
Figure 4.4.
A Feistel Cipher
4. Let the new 'right 32 bits'
R
1
be
X
.
5. Let the new 'left 32 bits'
L
1
be the previous 'right 32 bits'
R
0
.
6. Repeat the process from step 2 to step 5, except using
R
1
instead of
R
0
,
and
L
1
instead of
L
0
. This sequence of steps (step 2 to step 5) is known as a
round
of the block cipher. The function
f
used is often referred to as the
round
function
.
7. Repeat step 6 for as many rounds as specified by the algorithm design. Once
the last round (round number
m
) is completed then the last 'left 32 bits'
L
m
are
joined with the last 'right 32 bits'
R
m
to form the 64 bits of the ciphertext, which
is formed by concatenating
R
m
and
L
m
(in that order).
CHOOSING THE ROUND FUNCTION
Although it might look quite complicated at first, the algorithmic steps involved
in encrypting a plaintext block using a Feistel Cipher are actually very straight-
forward and easy to implement (we have just specified the algorithm, which
could easily now be converted into a computer programme). The difficult part
of designing a Feistel Cipher is the choice of the round function
f
. This function
needs to have several important properties that are beyond the scope of our
discussion. Indeed, most of the design work of any Feistel Cipher, such as DES,
concerns the choice of the round function.
DECRYPTION USING A FEISTEL CIPHER
The cleverness of the Feistel Cipher design concept only becomes clear when we
consider decryption. It turns out that decryption is almost the same as encryption