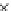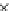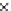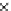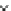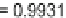Information Technology Reference
In-Depth Information
Fig. 3.11
Scalability of communication in terms of total number of messages sent with change in
number of fish for Algorithms 1-3 (
P19
.Bothetal.
2013
) (Republished from Both, A., Duckham,
M., Laube, P., Wark, T., and Yeoman, J., Decentralizedmonitoring of moving objects in a transporta-
tion network augmented with checkpoints,
The Computer Journal
, 2013, 56(12), pp. 1432-1449,
DOI: 10.1093/comjnl/bxs117, by permission of Oxford University Press)
other work included in this topic studies alternative versions of proposed algorithms,
explicitly aiming at optimization of running times. For instance Andersson et al. (
P5
.
2008
) proposed improved algorithms for leadership detection using additional index
structures (buckets) where the running times strongly depend on the characteristics
of the instances.
3.4 Related Work
This section summarizes further related work relevant to the topics covered in this
chapter. The chapter concludes with insights and lessons learned from both research
covered in this chapter and in related work.
Data mining for CMA
. Data mining techniques are proposed and applied in a wide
range of areas studying very diversemovement phenomena (
P15
. Laube et al.
2011b
).
Given the diversity of application problems and the multidisciplinary backgrounds
of the involved scientists, it is perhaps little surprising that there seems to be slow
progress towards an accepted general theory of movement mining. Nevertheless,
there is work aiming towards general taxonomies or ontologies of movement pat-
terns and movement mining tasks in general. Dodge et al. (
2008
) propose a taxonomy
for movement patterns, distinguishing between
generic patterns
(e.g. co-occurrence,
moving clusters) and
behavioral patterns
that are particular to certain types of
moving objects (e.g. foraging or flocking birds). Andrienko and Andrienko (
2007
)