Database Reference
In-Depth Information
Restricting access
This example is in some ways the inverse of the previous, but in addition it applies a
different mode in the ACL than in the Unix-style permissions to solve a more com‐
plex problem.
This time at our small publishing organization, one of our editors has been misbe‐
having and not rigorously checking articles from an academic institution that he used
to be involved with before accepting them to be published. The editor in question,
Jason Green, has thus been placed on review and is no longer allowed to make edits
to the
Nanotechnology Journal
; he is expected to just review the journal manually and
propose changes by email to another editor for review first.
Currently, the
Nanotechnology Journal
collection is configured like so:
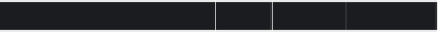
Collection Owner Group Mode
/db/journals/review/nanotechnology
admin editors rwxrwx---
We could reconfigure this collection with an ACL to prevent Jason Green from
changing the collection, while still allowing him the ability to view the collection.
Such a configuration for the
nanotechnology
collection could look like this:
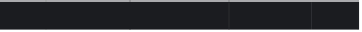
Collection
/db/journals/review/nanotechnology
ACL
Target type
ID
Access type
Mode
ACE:0
USER
jasongreen DENIED
-w-
Unix-style permissions
Owner
Group
Mode
admin
editors rwxrwx---
When Jason Green tries to access the
nanotechnology
collection, eXist checks the col‐
lection's ACL, iterating through each ACE in turn until it finds one that matches
Jason Green. In this case the first ACE matches the user
jasongreen
, so from here
one of two things happens:
• If Jason Green is trying to write to the collection (add or remove a document),
then the ACE
forbids
him from doing that, and he will
not
be allowed access.
• If Jason Green is trying to execute (open) and/or read (the contents of) the col‐
lection, then the ACE
does not
forbid him from doing that, as it only denies write
access to the collection. This ACE
does not match
the access request, so we fall















Search WWH ::

Custom Search