Java Reference
In-Depth Information
Figure 12.12
Basic XSS vector being executed by a vulnerable web application.
routines like blacklisting (disallowing known bad inputs) like the use of “<” or “>” or the <script>
tag. here are several XSS attacks that are created to bypass these ilters like encoding the mali-
cious input <script>alert('xss')</script> to form this:
%3Cscript%3Ealert('xss')%3C%2Fscript%3E
his is the encoded version of the malicious JavaScript that will execute after bypassing the vari-
ous blacklist ilters designed to disallow <script> or other JavaScript methods like “alert” and so
on. here are several XSS vectors that do not require the <script> tag to execute. Several XSS vec-
tors execute while being embedded in other HTML tags like IMG, BODY, and META. Some
examples of the same are as follows:
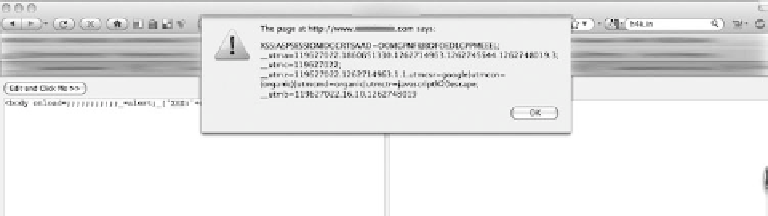
<body onload=;;;;;;;;;;;_=alert;_('XSS:'+document.cookie);;;;
he above vector executes the JavaScript on the loading of the page. his displays the text XSS and
the cookie value given to the user. Figure 12.13 shows the attack in action.
Another example of XSS attacks without the use of script tags is as follows:
<IFRAME SRC=”javascript:alert('XSS:'+document.cookie);”></IFRAME>
his attack injects an IFRAME into the Web application and displays the text “XSS” followed by
the session cookie. Figure 12.14 shows the attack in action.
here are several XSS vectors available all over the Internet. As XSS essentially relies on the
browser and its rendering of HTML and JavaScript, there are certain XSS vectors that will only
work on certain browser types. Security Specialist Robert “RSnake” Hansen has an XSS sheat
sheet,
*
which is considered an exhaustive set of XSS attack vectors that may be used by testers and
researchers to test Web applications for XSS vulnerabilities.
Figure 12.13
Use of th
e BoDY tag to perform an XSS attack.
*
he XSS Cheat Sheet may be found at http://www/ha.ckers.org/xss.html.



Search WWH ::

Custom Search