Java Reference
In-Depth Information
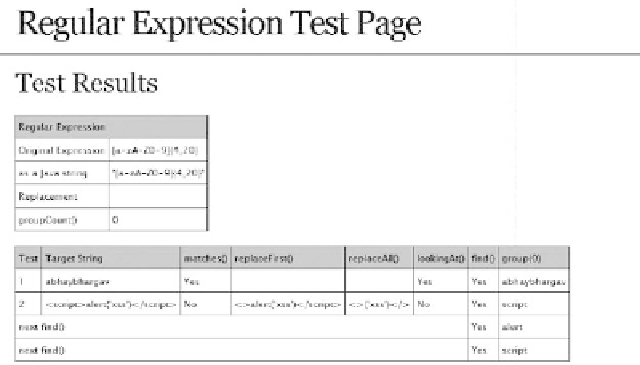
Figure 10.6
testing the Username Regular expression with the XSS Vector.
Whitelist validation, on the other hand, is quite the opposite when contrasted with the black-
list approach. A whitelist can be deined as a list or collection of entities that is trusted or explicitly
permitted. he whitelist method of validation is where the developer deines regular expressions
of known good characters that are explicitly allowed by the Web application—for instance, if a
username ield should contain only letters of the alphabet and numbers with only “-”, “_”, and “.”
With a minimum number of four characters and a maximum number of 25 characters, then a
regular expression for the same would be
[A-Za-z0-9 _ .-]{4,25}
. he application should be
conigured to only accept characters that match the following
known good
input for the username,
and any other input containing diferent characters like “<” or single quotes will be rejected by the
application.
he ideal method for validation of user input for a Web application is the whitelist method of
input validation. XSS attacks or SQL injection attacks can occur in several ways to circumvent
popular blacklisting validation methods. For instance, if the validation for a ield has been written
to disallow the “<SCRIPT>” tags in HTML, which are used to inject scripts into an application,
then the attacker could split the word SCRIPT in the tags to something like this:
<IMG SRC=JaVaScRiPt:alert('XSS')>
his XSS vector does not use the <SCRIPT> tag and still causes the XSS attack to be successful
against the application. Another example would be the use of a vector like this:
<BODY ONLOAD=alert('XSS')>
his kind of an attack would not require the use of a script tag at all for the execution of the script.
However, if a whitelist validation had been used in the ield, where only letters of the alphabet and
numbers (for a minimum of 4 and maximum of 30 characters} are allowed, with whitespaces, then
the following regular expression whitelist can be used to prevent injection-based attacks.
[a-zA-Z0-9\s]{4,30}
Search WWH ::

Custom Search