Java Reference
In-Depth Information
Figure 10.4
Using a Web application proxy, tamperData, to tamper with checkbox values.
unvalidated to the server, which would execute the user-entered JavaScript. We will explore this
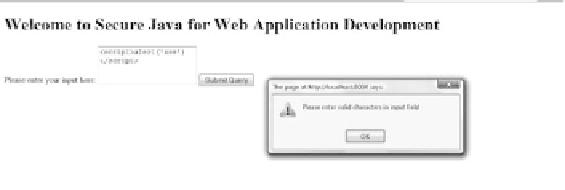
attack with the aid of two illustrations. Figure 10.5 illustrates the use of JavaScript validation
for the input ield. We can clearly observe that the JavaScript validation blocks the malicious
user input from being executed.
he JavaScript validation can easily be bypassed with the use of a Web application proxy. he
proxy intercepts all the communication between the client and Web server, and it also allows the
inputs to be manipulated.
One of the ideal methods of input validation is to canonicalize user input. Canonicalization
is the process of converting data structures to a universal data representation. For instance, the
input from a user may be in ASCII, Unicode, or another encoding format. It is important that
these vagaries be kept in mind and the input be reduced to its simplest possible representation.
his is useful from the security point of view, because it reduces the input to its simplest for-
mat and does not allow encoding from diferent formats to become potential script injection
vectors.
Figure 10.5
JavaScript validation used to prevent the entry of special characters in the input
ield.



Search WWH ::

Custom Search