Java Reference
In-Depth Information
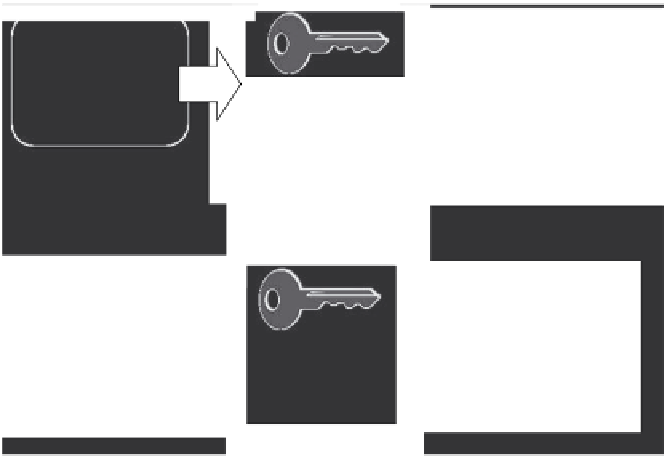
Cleartext
Ciphertext
Key A
“Secure Java for Web
Application
Development”
“_b64K4hutQ3VIWs8U
btMWQFAJjQh4DYyzn
Vo7HcjIndXITQEE2oca
pklkCVpMdHI
8um4_64b”
Encryption Algorithm-
Encryption Process
Ciphertext
Cleartext
Key A
“_b64K4hutQ3VIWs8U
btMWQFAJjQh4DYyzn
Vo7HcjIndXITQEE2oca
pklkCVpMdHI
8um4_64b”
“Secure Java for Web
Application
Development”
Encryption Algorithm-
Decryption Process
Figure 8.3
Symmetric key encryption—Use of the same key for encryption and decryption.
key belongs. Data encrypted with one key in the keypair can only be decrypted by the other key
of the same keypair. he private key may not be disclosed to anyone. Public key cryptography is
when a key is used to encrypt data and a diferent key is used for decryption of the same data.
For instance, Bob wants to send the message “I am coming to your oice on Friday” to Scott. He
will encrypt the message using Scott's public key and send it to Scott. his message can only be
decrypted by Scott, with his private key. herefore, Scott uses his private key to decrypt the mes-
sage. his example showed us that public key cryptography can be used to ensure the conidential-
ity of data. Bob encrypts the message with Scott's public key. his process ensures that the message
can only be decrypted with the use of Scott's private key. Asymmetric cryptography can also be
used for nonrepudiation. For instance, if Bob had encrypted the message with Bob's private key
instead of Scott's public key, then Scott can decrypt the same message only with Bob's public key.
Although this implementation does not ensure conidentiality (as Bob's public key is public), it
ensures nonrepudiation
*
and authentication, which means that there is no doubt that the message
came from Bob. his is so, because only Bob would have access to his private key. Figure 8.4 illus-
trates the use of public-private keypair for encryption.
here are some diferences between symmetric and asymmetric cryptography. hey are as follows:
◾
Symmetric cryptography is much faster than asymmetric cryptography. Symmetric cryptogra-
phy is known to be almost as much as 1000 times faster than asymmetric cryptography. his
makes asymmetric cryptography impractical for the encryption of a large quantum of data.
Symmetric cryptography does not provide authentication and nonrepudiation, unlike asym-
◾
metric cryptography. It is only meant for conidentiality of the data encrypted.
*
Nonrepudiation can be deined as the ability to assert the authorship of a message or information authored by
a second party, preventing the author from denying his own authorship.










Search WWH ::

Custom Search