Java Reference
In-Depth Information
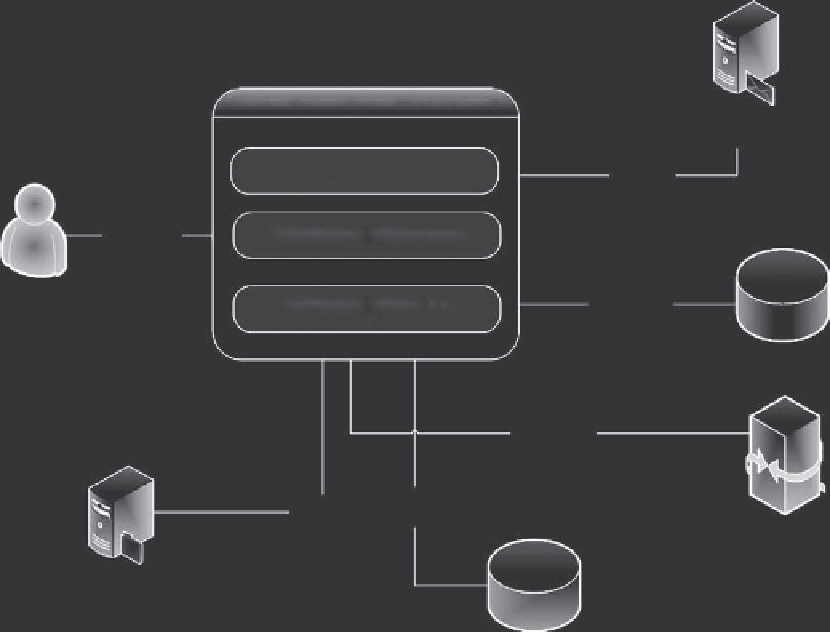
Panthera E-Commerce Application
Email and
Messaging Server
Presentation
TCP/IP
Business Logic
HTTP(S)
User with
Browser
TCP/IP
Data Access
Database
HTTPS
TCP/IP
TCP/IP
Payment
Gateway
File Server
Gift Card Database
Figure 6.2
Preliminary application architecture diagram—e-commerce application.
6.2.1 Panthera's Security Policies
During the workshop conducted by Jaguar InfoSolutions for Panthera's management and key
operational stakeholders, security policies were also discussed and identiied. Panthera's security
objectives for the envisaged e-commerce application are as follows:
◾
Critical information assets
◾
Financial impact
◾
Security compliance and regulation
6.2.1.1 Critical Information Assets
Panthera's management realizes that protection of the critical information assets identiied
in the previous process is one of their greatest policy objectives. Panthera's application would
be storing, processing, and/or transmitting all the critical information assets identiied in the
previous exercise. Critical and sensitive information like customer credit card information,
customer contact details, and order information is being handled by Panthera's e-commerce
application.
Search WWH ::

Custom Search