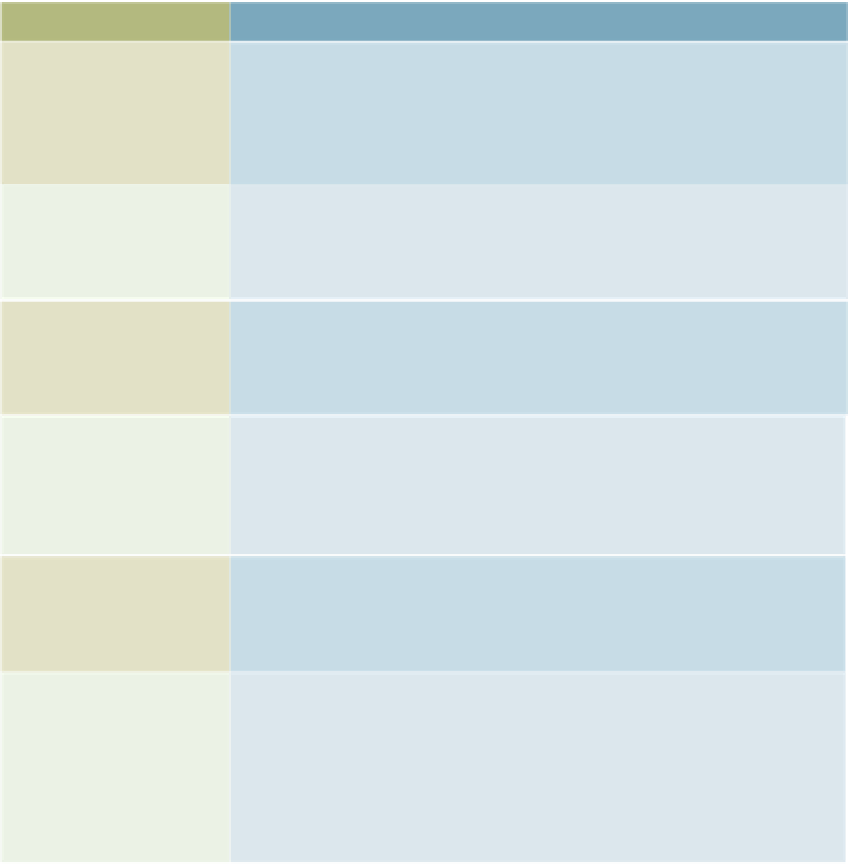Information Technology Reference
In-Depth Information
Table 13.1
Controls
Description
Input controls
Using Systems Controls to Enhance
Security
Maintain input integrity and security. Their purpose is to
reduce errors while protecting the computer system against
improper or fraudulent input. Input controls range from using
standardized input forms to eliminating data-entry errors and
using tight password and identification controls.
Processing controls
Deal with all aspects of processing and storage. The use of
passwords and identification numbers, backup copies of data,
and storage rooms that have tight security systems are
examples of processing and storage controls.
Output controls
Ensure that output is handled correctly. In many cases, output
generated from the computer system is recorded in a file that
indicates the reports and documents that were generated, the
time they were generated, and their final destinations.
Database controls
Deal with ensuring an efficient and effective database system.
These controls include the use of identification numbers and
passwords, without which a user is denied access to certain
data and information. Many of these controls are provided by
database management systems.
Telecommunications
controls
Provide accurate and reliable data and information transfer
among systems. Telecommunications controls include
firewalls and encryption to ensure correct communication
while eliminating the potential for fraud and crime.
Personnel controls
Make sure that only authorized personnel have access to certain
systems to help prevent computer-related mistakes and crime.
Personnel controls can involve the use of identification numbers
and passwords that allow only certain people access to particular
data and information. ID badges and other security devices
(such as smart cards) can prevent unauthorized people from
entering strategic areas in the information systems facility.
After controls are developed, they should be documented in standards manuals that in-
dicate how the controls are to be implemented. They should then be implemented and
frequently reviewed. It is common practice to measure the extent to which control techniques
are used and to take action if the controls have not been implemented.
Many companies use ID badges to
prevent unauthorized access to
sensitive areas in the information
systems facility.
(Source: Michael Newman/Photo
Edit.)