Information Technology Reference
In-Depth Information
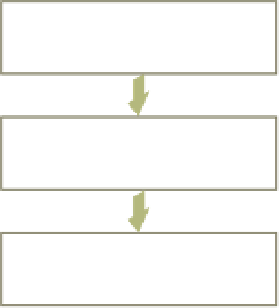
Figure 13.2
Identification
The Levels of the Sign-On
Procedure
Verification
Authorization
•
With
interactive processing,
people directly interact with the processing component
of the system through terminals or networked PCs. With a
menu-driven system
(see Figure 13.3), users simply pick what they want to do from a list of alternatives. Most
people can easily operate these types of systems. They select an option or respond to
questions (or prompts) from the system, and the system does the rest.
menu-driven system
A system in which users simply pick
what they want to do from a list of
alternatives.
Figure 13.3
Menu-Driven System
A menu-driven system allows you to
choose what you want from a list of
alternatives.
Order Processing
Purchasing
Accounting
General
ledger
Income
statement
Balance
sheet
Other
accounting
information
Main menu
Submenu
•
Many designers incorporate a
help facility
into the system or applications program. When
users want to know more about a program or feature or what type of response is expected,
they can activate the help facility.
help facility
A program that provides assistance
when users want to know more
about a program or feature or what
type of response is expected.
•
Computer programs can develop and use
lookup tables
to simplify and shorten data
entry. For example, if you are entering a sales order for a company, you can type its
abbreviation, such as ABCO. The program will then go to the customer table, normally
stored on a disk, and look up all the information pertaining to the company abbreviated
ABCO that you need to complete the sales order.
lookup tables
Tables containing data that
computer programs can develop
and use to simplify and shorten data
entry.
•
With a
restart procedure,
users can restart an application where it stopped in case the
application crashed or had problems.
restart procedures
Simplified processes to access
an application from where it
stopped.
Design of System Security and Controls
In addition to considering the system's interface and user interactions, designers must also
develop system security and controls for all aspects of the system, including hardware, soft-
ware, database systems, telecommunications, and Internet operations. These key considera-
tions involve error prevention, detection, and correction; disaster planning and recovery;
and systems controls. Some small and medium-sized corporations, for example, are buying