Information Technology Reference
In-Depth Information
that the key be kept secret from possible interceptors. A hacker who obtains the key by
whatever means can recover the original message from the encrypted data.
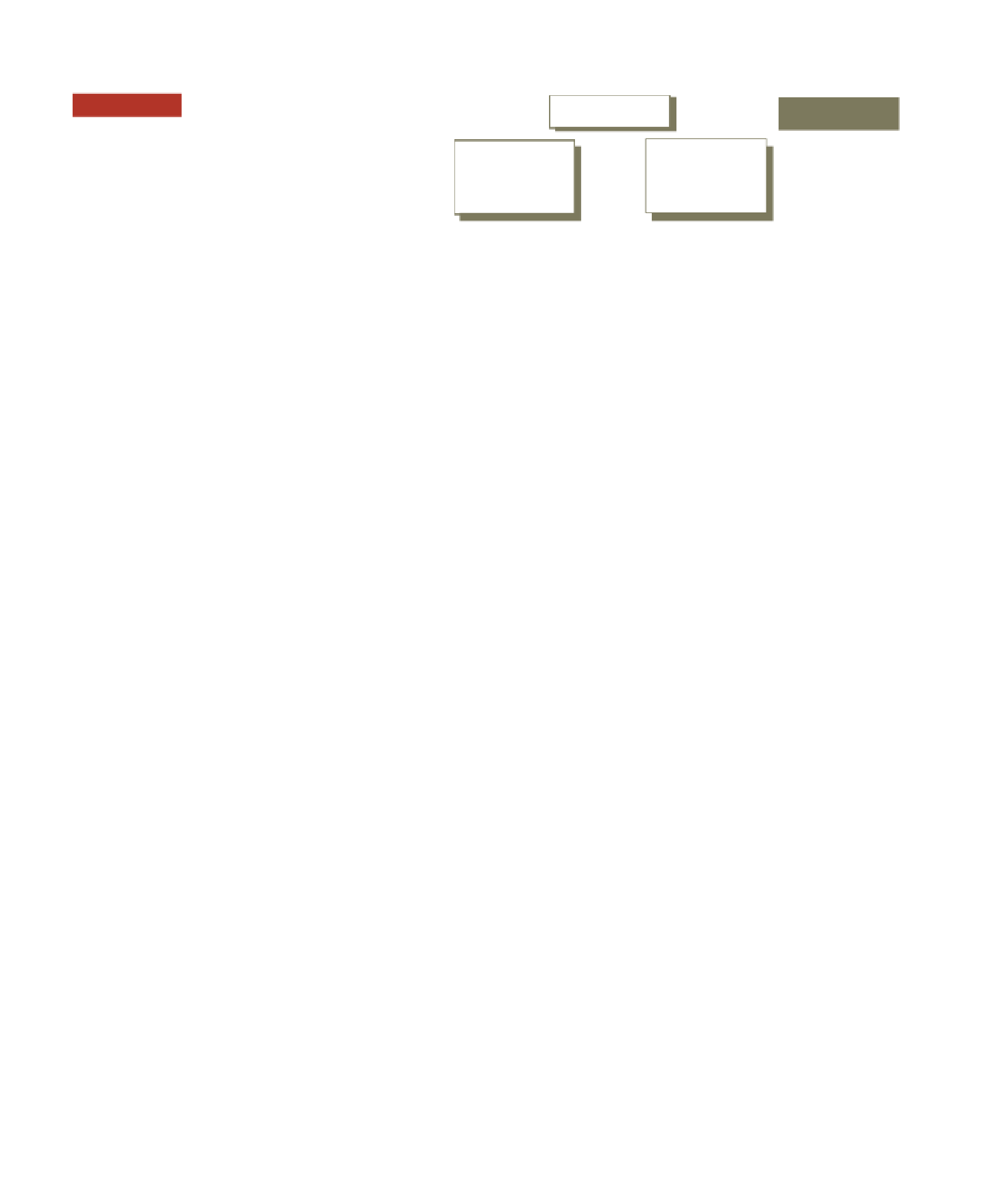
Figure 6.12
Encrypted text
Unencrypted text
The Encryption Process
Original
message:
Hello John
Encryption
software or
hardware
Decryption
software or
hardware
Hello John
Ciphertext
?8AA;7%Bx
Encryption methods rely on the limitations of computing power for their security—if
breaking a code requires too much computing power, even the most determined hacker
cannot be successful. In an alarming breakthrough, two research groups in Australia and
China working independently have built laser-based quantum computers that can implement
Shor's algorithm, a mathematical routine capable of cracking modern encryption methods.
This development raises the potential that others could build such computers and break the
codes that protect our national security secrets, banking transactions, and business data.
39
Securing Wireless Networks
WEP and WPA are the two main approaches to securing wireless networks such as Wi-Fi
and WiMAX.
Wired equivalent privacy (WEP)
used encryption based on 64-bit key, which
has been upgraded to a 128-bit key. WEP represents an early attempt at securing wireless
communications and is not difficult for hackers to crack. Most wireless networks now employ
the
Wi-Fi Protected Access (WPA)
security protocol that offers significantly improved pro-
tection over WEP.
The following steps, while not foolproof, help safeguard a wireless network:
•
Connect to the router and change the default logon (admin) and password (password)
for the router. These defaults are widely known by hackers.
•
Create a service set identifier (SSID). This is a 32-character unique identifier attached to
the header portion of packets sent over a wireless network that differentiates one network
from another. All access points and devices attempting to connect to the network must
use the same SSID.
•
Configure the security to WEP or WPA, preferably WPA if all devices connected to the
network are WPA compatible. Surprisingly, many routers are shipped with encryption
turned off.
•
Disable SSID broadcasting. By default, wireless routers broadcast a message
communicating the SSID so wireless devices within range (such as a laptop) can identify
and connect to the wireless network. If a device doesn't know the wireless network's
SSID, it cannot connect. Disabling the broadcasting of the SSID will discourage all but
the most determined and knowledgeable hackers.
•
Configure each wireless computer on the network to access the network by setting the
security to WEP or WPA and entering the same password entered to the router.
War driving
involves hackers driving around with a laptop and antenna trying to detect
insecure wireless access points. Once connected to such a network, the hacker can gather
enough traffic to analyze and crack the encryption. On a WEP-encrypted network and with
85,000 packets to analyze, there is about a 95 percent probability that the hacker can crack
the code in less than two minutes using the program aircrack-ptw running on an ordinary
45 million credit and debit card customers of TJX, the parent company of T.J. Maxx,
Marshalls, Winners, Home Goods, and other retailers.
41
Wired equivalent privacy (WEP)
An early attempt at securing wire-
less communications based on
encryption using a 64- or 128-bit key
that is not difficult for hackers to
crack.
Wi-Fi Protected Access (WPA)
A security protocol that offers
significantly improved protection
over WEP.