Graphics Reference
In-Depth Information
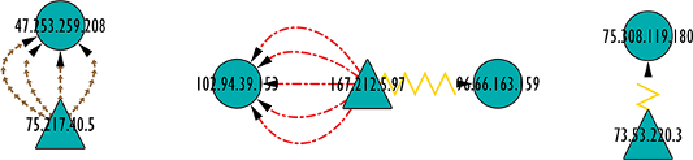
Let's assume that DNS and FTP attacks are important to identify. Only four
DNS Overflow attacks between a single source and target are hidden in the
field of two-node components on the left side of
Figure 9-4
, and enlarged in
Figure 9-6
. Similarly, only two FTP attacks (shown as a yellow zigzag link)
exist in this data, hidden in two different small components.
Figure 9-6:
Some specific specialized attacks may be easy to miss in the
larger graph shown in
Figure 9-4
.
E-mail Relationships
Social networks are full of fuzzy relationships. You can extract and
transform this data into multiple different link types to explore and better
understand the relationships. Following are some of the many different
sources of social data that may contain multiple types of relationships:
• An address book or directory may provide metadata such as
department, tenure, and responsibilities of a person.
• A sales system or customer relationship management (CRM) system
may contain metadata such as job title, management level,
responsibilities, and so on.
• Content analysis (for example, keywords in an e-mail title) may indicate
useful information, such as products or opportunities.
• E-mail addresses can be used to differentiate between types of e-mails
(for example,
bob@us.ibm.com
is likely a different kind of relationship
than
bob789@gmail.com
).
• From, To, CC, and BCC can be used to identify how close the
relationship is. A From-To relationship indicates a direct
communication between two people. A From-CC relationship indicates
a potentially weaker relationship, where a person may simply be
informed of status.